Riskware/GoneSixty!Android
 Analysis
Analysis
Riskware/GoneSixty!Android targets Android mobile phones. It advertises
as being capable to upload personal data found on the phone (contacts, SMS, calls etc)
onto a remote web site in less than 60 seconds.
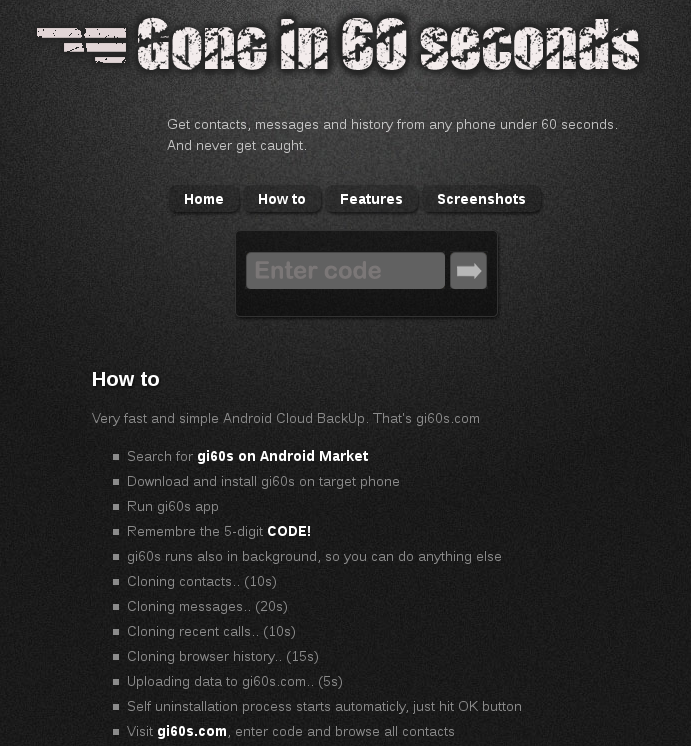
Figure 1. The remote web site where information is uploaded.
This application is risky when installed on a phone without the owner's consent.
To install on a phone, a spy must have physical access to the phone. The spy
might also install GoneSixty using an already installed backdoor running on the phone,
or using some social engineering to convince the victim he/she must install the application.
Those are generic possibilities to install any spying tool, but there hasn't been
any report of malicious installation using such techniques.
Technical Details
When the application is launched, it uploads all information to a remote website:
http://[REMOVED]s.com/upload.phpThe information is POSTed using HTTP, where the POST data consists of the following value pairs:
- code: generated value of the code to retrieve information on the remote website
- data: private information is Base64 encoded:
- contacts: display name and phone number
- sms: address, type, date and body
- call: number, type, data and duration
- url: visited url
- generate a random integer
- perform a MD5 hash of the integer
- take the 5 first digits of the hash
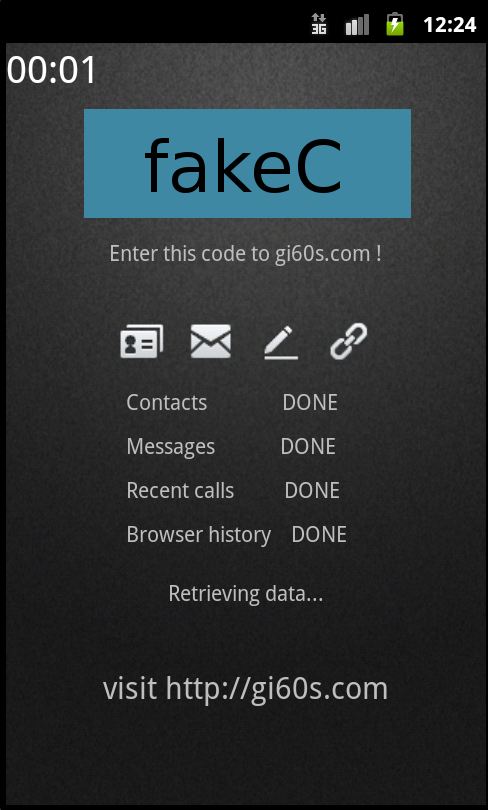
Figure 2. Application is uploading data. Displays code to retrieve data
The spy may they view the stolen data:
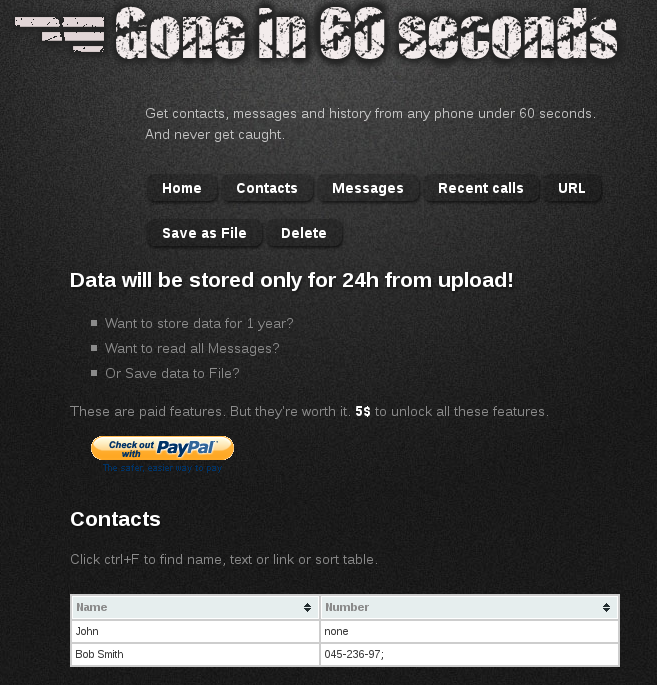
Figure 3. Uploaded data visible on the remote website
Finally, the application automatically tries to uninstall:
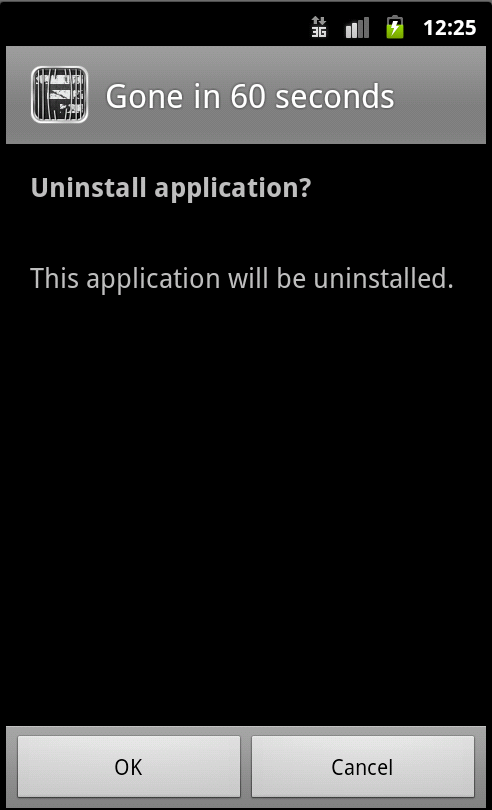
Figure 4. The application automatically triggers uninstallation. Physical access to the phone is however required to accept uninstallation or not
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.