W32/PWS.Y!tr
 Analysis
Analysis
W32/PWS.Y!tr is a highly generic detection for a trojan and possible attacker tools.
Since this is a generic detection, malware that are detected as W32/PWS.Y!tr may have varying behaviour.
Below are examples of some of these behaviours:
- During our tests, some instances of this malware may drop any of the following file(s):
- %AppData%\1337\21.01.18.exe : This file is currently detected as W32/PWS.Y!tr.
- %AppData%\1337\joinResult.exe : This file is currently detected as W32/PWS.Y!tr.
- %AppData%\1337\mm.exe : This file is currently detected as W32/CoinMiner.DQ!tr.
- %AppData%\system\svchost.exe : This file is currently detected as Riskware/BitMiner.
- %RootDir%\Log\build.exe : This file is currently detected as Riskware/BitCoinMiner.
- %ProgramData%\Windows\System32\x64\afdf598d77d6cbb1453204382b7a3c48e7b20daf1efc336c03ead96a8e36a70c : This file is currently detected as PossibleThreat.
- %ProgramData%\olly.exe : This file is currently detected as PossibleThreat.
- %ProgramData%\Windows\System32\x64\afdf598d77d6cbb1453204382b7a3c48e7b20daf1efc336c03ead96a8e36a70c : This file is currently detected as PossibleThreat.
- %AppData\1337\Fan.exe : This file is currently detected as Generik.JEPNUSQ!tr.
- %ProgramFiles%\miped\qwiget\this is wiiiget!.exe : This file is currently rated none malicious application.
- %SystemDrive%\log\shfhc.vbs : At the time of the test this file failed to be dropped.
- %Temp%\d3dx11_31.dll : At the time of the test this file failed to be dropped.
- This malware may connect to any of the following remote sites(s):
- mosol{Removed}.com
- xm{Removed}.pool.minergate.com
- iplogge{Removed}.com
- hxxp://mosol{Removed}.com/hfUJRMDK64HDF/gate.php
- hxxp://mosol{Removed}.com/hfUJRMDK64HDF/file/relse.exe
- This malware may apply any of the following registry modification(s):
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- Fant = %SystemDrive%\log\shfhc.vbs
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- This is wiiiget! = %ProgramFiles%\miped\qwiget\this is wiiiget!.exe
- Directx 11 = rundll32 %Temp%\d3dx11_31.dll includes_func_runnded
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- Some samples belonging to this detection have attacker tools like behavior, much like a Riskware.
- Some instance of this detection may also have coin mining capabilities.
- Some instances of this malware may displays any of the following user interface:
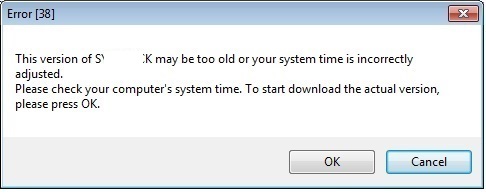
- Figure 1: Prompt Message.
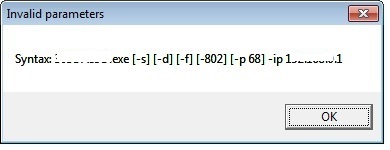
- Figure 2: Prompt Message.
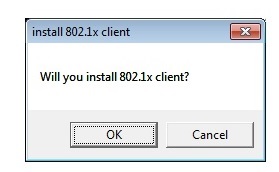
- Figure 3: Prompt Message.
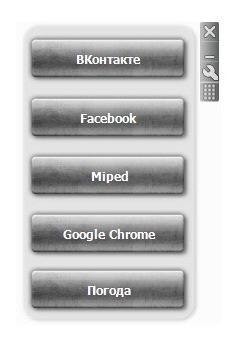
- Figure 4: User Interface.
- Figure 5: User Interface.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |