Android/IknoSpy.A!tr.spy
 Analysis
Analysis
Android/IknoSpy.A!tr.spy is a piece of malware targetting Android mobile phones.
The malicious package is downloaded in the background by a legitimate Fonts application found on Google Play. After installation, the application can't be seen in the phone's main menu. In the background, it registers the infected phone with a server and spies on incoming calls and SMS messages which are forwarded to the server. It can also toggle the GPS status of the application and send location information to the attacker's server upon request
Technical Details
The main application is called "Ikno" and comes in the package "com.sam.ikno" It can't be seen in the main applications menu, only in the list of installed applications in the Settings menu as seen in Fig1
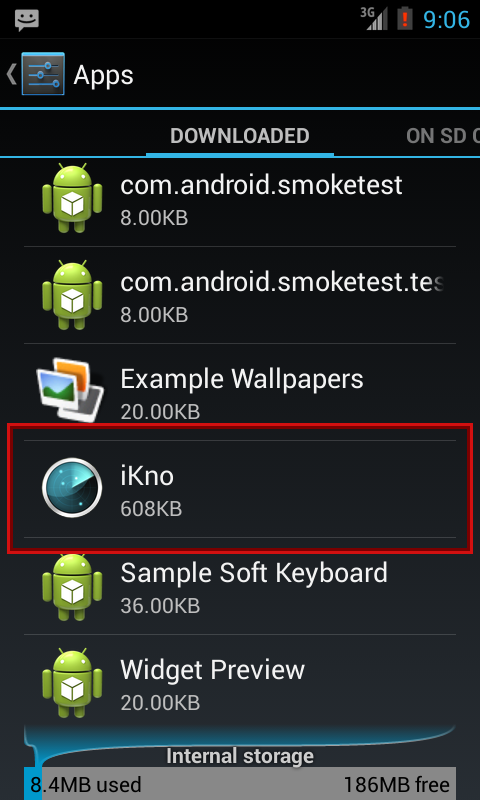
Fig1 : Ikno application seen in the Settings menu
The spying application can be activated by dialling '1985' on the phone.
When dialled, the user sees a screen as seen in Fig2 which is used to register the phone with the attacker's server.
This is done by sending an HTTP POST request to
http://www.[REMOVED].com/new_user_device.phpwith the parameters
serial=[IMEI]&name=[NAME]&email=[EMAIL]&password=[PWD]where the values of NAME, EMAIL and PWD are entered by the user.
The user is shown the response received from the server.
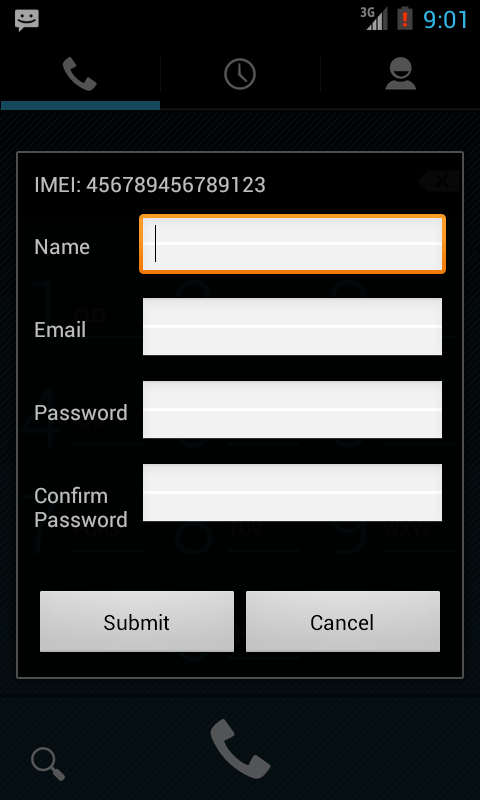
Fig2 : Application registration screen
Next, the application monitors incoming and outgoing calls and SMS messages on the phone.
The application maintains a log of these activities in a database called 'logsdb' in a table named 'tbl_log'.
Each time one of these activities takes place, an entry is added to the 'tbl_log' table of the 'logsdb' database.
Finally, a timer is set to send an HTTP request to
http://www.[REMOVED].com/ikno/get_pending_requests.php?accid=[IMEI]every 3 minutes.
The malware expects a response in the format
"REQ_type" : [REQ], "poll_duration": [P_DUR], "status": [STATUS]where REQ can be "LOC" or "CAM"
If REQ = LOC, the current GPS location of the phone is sent in an HTTP POST request to
http://www.[REMOVED].com/ikno/insertlog2.phpwith parameters
type=LOC&origin=[IMEI]&body=[LATITUDE]+","+[LONGITUDE]&duration=×tamp=[Current_Time]&devserial=[IMEI]&smstype=&appid=20120109_TERA
If REQ = CAM, a picture is taken with the phone's camera, and saved to the table "tbl_images" in the logsdb database.
The function that sends these images to the attacker's server is not called/used anywhere in the package.
The contents of the logsdb database are sent periodically in a POST request to
http://www.[REMOVED].com/ikno/insertlog2.phpwith the parameters
type=[TYPE]&origin=[NUM]&body=[BODY]&duration=[DUR]×tamp=[TIME]&devserial=[IMEI]&smstype=[STYPE]&appid=20120109_TERAwhere
- TYPE = CALL or SMS
- NUM = Sender/Recepient of Incoming/Outgoing SMS or "Draft SMS" in case of a draft or Source/Destination of Incoming/Outoing Call
- BODY = SMS message body or "OUTGOING CALL Duration: " (in case of outgoing calls) or "INCOMING CALL Duration: " (in case of incoming calls)
- DUR = ""
- TIME = Time of SMS or outgoing or incoming call
- STYPE = 2 in case of outgoing SMS messages, 3 in case of a Draft SMS
Permissions required by the application:
- RECEIVE_BOOT_COMPLETED
- SEND_SMS
- RECEIVE_SMS
- READ_SMS
- WRITE_SMS
- RECEIVE_MMS
- INTERNET
- PROCESS_OUTGOING_CALLS
- READ_PHONE_STATE
- READ_CONTACTS
- ACCESS_NETWORK_STATE
- ACCESS_FINE_LOCATION
- ACCESS_COARSE_LOCATION
- CAMERA
- MODIFY_AUDIO_SETTINGS
- RECORD_AUDIO
- WRITE_EXTERNAL_STORAGE
- CALL_PHONE
Certificate information:
- Owner: CN=Technoreap Solutions, L=Nairobi
- Issuer: CN=Technoreap Solutions, L=Nairobi
- Serial number: 4f8b2290
- Valid from: Sun Apr 15 21:33:36 CEST 2012 until: Thu Apr 09 21:33:36 CEST 2037
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.