Android/Crosate.A!tr
 Analysis
Analysis
Android/Crosate.A!tr is a sophisticated bot and spying malware for Android devices.
It poses as a Flash Player viewer, but in background it steals SMS, sends SMS, sends data concerning calls, sends your contacts lists and answers to various botmaster commands.
Additionally, the malware tries to steal your credentials when you buy an application or login into the mobile banking account of a Russian bank.
Technical Details
The malicious application is typically named Adobe Flash Player.
It comes packaged as com.adobe.flpview.
As soon as it is launched the malware sends two SMS to Russian numbers:
+7926200xxxx 38 +7903767xxxx balIt asks the end-user to be installed as "device administrator" (see Figure 1).
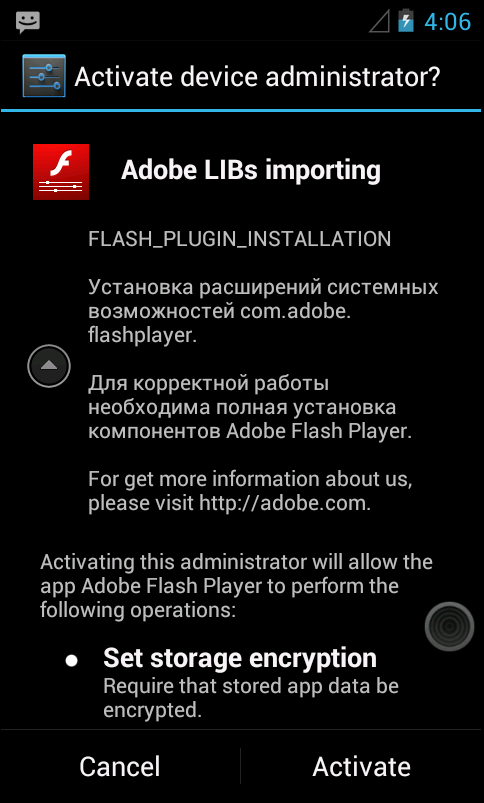
Figure 1. The malware asks for permission to be installed as device administrator
On Android, the device administrator API helps implement security applications at system level. To uninstall a device administrator, the end-user must go to Settings > Security and select the correct device administrator for disabling.
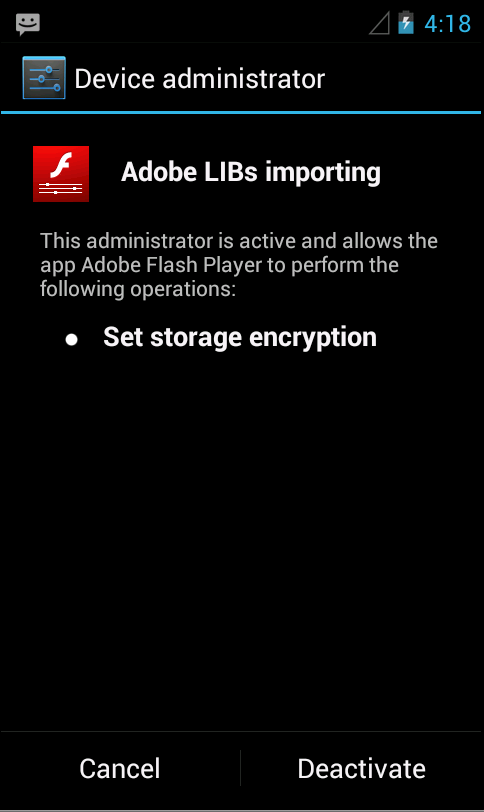
In the case of Android/Crosate.A!tr, the problem is that the malware prevents removal as device administrator.
When the end-user tries to unregister the device administrator, it waits for 7 seconds, then displays a warning message "Do you want device factory reset?\n\nClick \"Yes\" and your's device will reboot and \"No\" for cancel.".
Figure 2. Trying to uninstall the Crosate device administrator...
Then, it displays the following activity (see Figure 3). If you click on Cancel, you cancel unregistering the device administrator. And if you click on "Delete Plugin", despite any password you enter, the activity always displays "Deleting error.\n\nWrong password of local storage. Please, try again.", and the device admin is not unregistered.
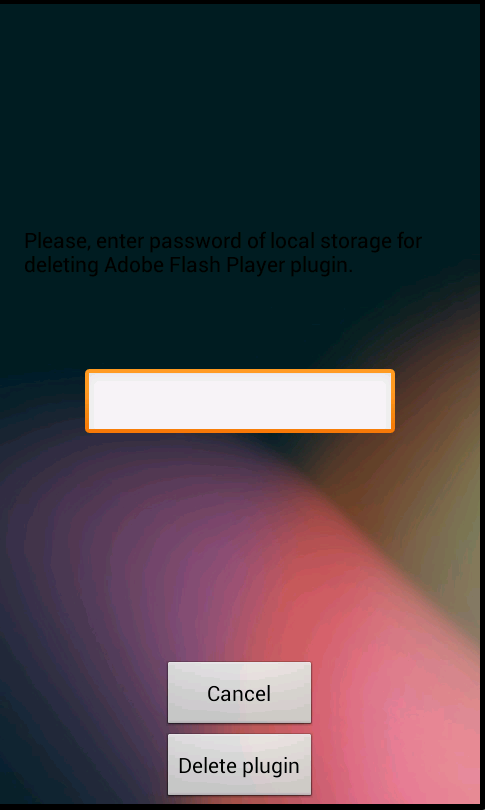
Figure 3. ...leads to a screen which asks for a code
Trick to disable the device administrator: In some cases, the following trick has been found successful to remove the device administrator. It consists at sending several SMS to the device (for instance via telnet) or finding anyother way to have the com.adobe.flpview process crash several times. Having the process crash only once is not sufficient, because it is normally relaunched immediately. However, after several crashes, the system refuses to re-launch it, and the system logs display a message saying it won't re-launch.
Once this has happened, the malware can be unregistered as device administrator, and then uninstalled.
The malware communicates with a remote server via HTTP:
http://[CENSORED].10/french/gate.phpThis remote server is named "Reich Server Gate", and its URL is stored in a file named /data/data/com.adobe.flpview/files/Reich_ServerGate.
Generally speaking, it sends HTTP GET to this server with various information as arguments.
Locally, it strores information in various files in directory /data/data/com.adobe.flpview/files/.
The malware shows the following functionalities:
- sending incoming SMS to the remote server. The HTTP GET sent to the server contains the type "h=in_sms".
- sending outgoing SMS. The HTTP GET request contains the type "h=out_sms".
- stealing SMS: in that case, SMS are not seen on the device. The request contains argument "h=stealed_sms".
- package info: information regarding packages which are currently running on the device. The HTTP GET request contains the type "h=request".
- sending the incoming call's phone number. This corresponds to h=in_calls. (See class FFF000).
- sending the phone number of an outgoing call. This is sent via HTTP GET to the server, with h=out_call
- blocking an incoming call. In that case an HTTP GET message is sent to the service with argument h=blocked_call and the blocked phone number.
- recording a call. The record is stored on the SD card in a file named .andro_secure.
- sending contacts information. The HTTP GET contains h=contacts
- detects if mobile application from the Russian sberbank is running, and will perform an action which has been reversed yet.
- calling a given phone number or USSD
http://[CENSORED].10/french/gate.php/a=In some cases, the malware sends SMS messages to a "Reich SMS Gate". The phone number is stored in a file named Reich_SMSGate in directory /data/data/com.adobe.flpview/files. By default, the SMS Gate is a Russian number. The SMS starts with:&b= &c= &d= &e= &f= &g= &prefix= &h= &i=
KEY CODEundefinedBOT IDundefinedThe Key Code is some obscure prefix, configured in /data/data/com.adobe.flpview/keyCode. By default zkazka. The Bot Id is an identifier to identify the victim's phone.
The malware uses the following parameters:
Name Possible values ===== ================ config lock stop/work BotPhone victim's phone number BotID BotNetwork Android BotLocation us Reich_ServerGate http://[CENSORED]/french/gate.php BotVer 6.0cs c 1234567890 BotPrefix french FkData keyCode zkazka server start/stop Reich_SMSGate 79[CENSORED] lending http://[CENSORED] w * or NOFILTER MacrosAState A MacrosData 79[CENSORED] pm_setts 79[CENSORED] forceZ on/off calls_data package pmfkz fuckav0Each of these parameters corresponds to a file in /data/data/com.adobe.flpview/files.
The malware contains bad language targeted at AV vendors ;) It uses method and class name obfuscation.
The malware contains the following files:
res/drawable/authorization_footer_logo_background.xml res/drawable/authorization_footer_logo_without_corners_background.xml res/drawable/authorization_input_pincode_footer.xml res/drawable/authorization_logo_background.xml res/drawable/black_gradient.xml res/drawable/box.xml res/drawable/btn_c.png res/drawable/btn_enter_green.xml res/drawable/btn_enter_green_background.xml res/drawable/btn_enter_green_disabled.xml res/drawable/btn_enter_green_tap.xml res/drawable/btn_n.png res/drawable/down.png res/drawable/fbi.png res/drawable/field_inactive.png res/drawable/field_inactive1.png res/drawable/pm_ok.xml res/drawable/pmok_state.xml res/drawable/progress_horizontal_holo_light.xml res/drawable/progress_indeterminate_horizontal_holo_light.xml res/drawable/tab_indicator_holo.xml res/layout/activity_check.xml res/layout/activity_ct.xml res/layout/activity_main.xml res/layout/activity_pm.xml res/layout/activity_pm_err.xml res/layout/activity_pm_ok.xml res/layout/activity_sb.xml res/layout/activity_zl.xml res/xml/device_admin_data.xml AndroidManifest.xml resources.arsc res/drawable-hdpi/back.png res/drawable-hdpi/bg.png res/drawable-hdpi/bg_cell_green.png res/drawable-hdpi/bg_login.jpg res/drawable-hdpi/bg_transparent.png res/drawable-hdpi/btn_bill.9.png res/drawable-hdpi/btn_bill_tap.9.png res/drawable-hdpi/btn_confirm.9.png res/drawable-hdpi/btn_confirm_inactive.9.png res/drawable-hdpi/btn_confirm_tap.9.png res/drawable-hdpi/btn_exit.9.png res/drawable-hdpi/btn_exit_tap.9.png res/drawable-hdpi/ic_launcher.png res/drawable-hdpi/logo_.png res/drawable-hdpi/progress_bg_holo_light.9.png res/drawable-hdpi/progress_primary_holo_light.9.png res/drawable-hdpi/progress_secondary_holo_light.9.png res/drawable-hdpi/progressbar_indeterminate_holo1.png res/drawable-hdpi/progressbar_indeterminate_holo2.png res/drawable-hdpi/progressbar_indeterminate_holo3.png res/drawable-hdpi/progressbar_indeterminate_holo4.png res/drawable-hdpi/progressbar_indeterminate_holo5.png res/drawable-hdpi/progressbar_indeterminate_holo6.png res/drawable-hdpi/progressbar_indeterminate_holo7.png res/drawable-hdpi/progressbar_indeterminate_holo8.png res/drawable-hdpi/tab_selected_focused_holo.9.png res/drawable-hdpi/tab_selected_holo.9.png res/drawable-hdpi/tab_selected_pressed_holo.9.png res/drawable-hdpi/tab_unselected_focused_holo.9.png res/drawable-hdpi/tab_unselected_holo.9.png res/drawable-hdpi/tab_unselected_pressed_holo.9.png res/drawable-hdpi/window_kurs.png res/drawable-hdpi/window_logo.png res/drawable-hdpi/window_logo_wo_logo.png res/drawable-hdpi/window_pass.png res/drawable-ldpi/back.png res/drawable-ldpi/bg.png res/drawable-ldpi/bg_cell_green.png res/drawable-ldpi/bg_cell_white.png res/drawable-ldpi/bg_login.png res/drawable-ldpi/bg_transparent.png res/drawable-ldpi/bookmark.png res/drawable-ldpi/btn_bill.9.png res/drawable-ldpi/btn_bill_tap.9.png res/drawable-ldpi/btn_confirm.9.png res/drawable-ldpi/btn_confirm_inactive.9.png res/drawable-ldpi/btn_confirm_tap.9.png res/drawable-ldpi/btn_exit.9.png res/drawable-ldpi/btn_exit_tap.9.png res/drawable-ldpi/btn_location_tap.png res/drawable-ldpi/btn_menu_green.9.png res/drawable-ldpi/btn_menu_tap.9.png res/drawable-ldpi/btn_menu_white.9.png res/drawable-ldpi/btn_mobile.png res/drawable-ldpi/btn_radiobtn.png res/drawable-ldpi/btn_radiobtn_checked.png res/drawable-ldpi/btn_right_gray.9.png res/drawable-ldpi/btn_right_green.9.png res/drawable-ldpi/btn_settings.png res/drawable-ldpi/btn_settings_tap.png res/drawable-ldpi/cabinet.png res/drawable-ldpi/check.png res/drawable-ldpi/check1.png res/drawable-ldpi/check1_complite.png res/drawable-ldpi/check2.png res/drawable-ldpi/check_tap.png res/drawable-ldpi/cosmostv.png res/drawable-ldpi/dimm.png res/drawable-ldpi/dimm_active.png res/drawable-ldpi/domolink.png res/drawable-ldpi/dot_big.png res/drawable-ldpi/dot_small.png res/drawable-ldpi/eniseytelecom.png res/drawable-ldpi/enter_button.9.png res/drawable-ldpi/enter_button_green.9.png res/drawable-ldpi/facebook_icon.png res/drawable-ldpi/fb_social_btn.png res/drawable-ldpi/file.png res/drawable-ldpi/font_bigger.png res/drawable-ldpi/font_bigger_inactive.png res/drawable-ldpi/font_bigger_tap.png res/drawable-ldpi/font_smaller.png res/drawable-ldpi/font_smaller_inactive.png res/drawable-ldpi/font_smaller_tap.png res/drawable-ldpi/green.9.png res/drawable-ldpi/green_small.9.png res/drawable-ldpi/ic_launcher.png res/drawable-ldpi/icn_a_express.png res/drawable-ldpi/icn_arrow_big.png res/drawable-ldpi/icn_arrow_big_up.png res/drawable-ldpi/icn_arrow_grey.png res/drawable-ldpi/icn_arrow_grey_left.png res/drawable-ldpi/icn_arrow_mini.png res/drawable-ldpi/icn_arrow_mini_left.png res/drawable-ldpi/icn_block_card.png res/drawable-ldpi/icn_deposit.png res/drawable-ldpi/icn_deposit_open.png res/drawable-ldpi/icn_fixed.png res/drawable-ldpi/icn_history_credit.png res/drawable-ldpi/icn_info.png res/drawable-ldpi/icn_info_tap.png res/drawable-ldpi/icn_internet.png res/drawable-ldpi/icn_loans.png res/drawable-ldpi/icn_maestro.png res/drawable-ldpi/icn_main_cards.png res/drawable-ldpi/icn_main_credits.png res/drawable-ldpi/icn_main_deposit.png res/drawable-ldpi/logo_.png res/drawable-ldpi/panel.png res/drawable-ldpi/shadow.png res/drawable-ldpi/shadow_down.png res/drawable-ldpi/window_kurs.png res/drawable-ldpi/window_logo.png res/drawable-ldpi/window_pass.png res/drawable-mdpi/avon.png res/drawable-mdpi/back.png res/drawable-mdpi/balloon_black.9.png res/drawable-mdpi/bg.png res/drawable-mdpi/bg_cell_green.png res/drawable-mdpi/bg_cell_white.png res/drawable-mdpi/bg_login.png res/drawable-mdpi/bg_transparent.png res/drawable-mdpi/bookmark.png res/drawable-mdpi/btn_arrow.9.png res/drawable-mdpi/btn_arrow_tap.9.png res/drawable-mdpi/btn_bill.9.png res/drawable-mdpi/btn_bill_tap.9.png res/drawable-mdpi/btn_confirm.9.png res/drawable-mdpi/btn_confirm_inactive.9.png res/drawable-mdpi/btn_confirm_tap.9.png res/drawable-mdpi/btn_exit.9.png res/drawable-mdpi/btn_exit_tap.9.png res/drawable-mdpi/btn_file_book.png res/drawable-mdpi/btn_file_book_tap.png res/drawable-mdpi/btn_grey.9.png res/drawable-mdpi/btn_howto_enter1.9.png res/drawable-mdpi/btn_inf.png res/drawable-mdpi/btn_inf_tap.png res/drawable-mdpi/btn_left_gray.9.png res/drawable-mdpi/btn_left_green.9.png res/drawable-mdpi/btn_location.png res/drawable-mdpi/btn_location_tap.png res/drawable-mdpi/btn_menu_green.9.png res/drawable-mdpi/btn_menu_tap.9.png res/drawable-mdpi/btn_menu_white.9.png res/drawable-mdpi/btn_right_gray.9.png res/drawable-mdpi/btn_right_green.9.png res/drawable-mdpi/enter_button.9.png res/drawable-mdpi/enter_button_green.9.png res/drawable-mdpi/ic_launcher.png res/drawable-mdpi/logo_.png res/drawable-mdpi/panel.png res/drawable-mdpi/panel_green_history.png res/drawable-mdpi/separator_small.png res/drawable-mdpi/shadow.png res/drawable-mdpi/shadow_down.png res/drawable-mdpi/window_kurs.png res/drawable-mdpi/window_logo.png res/drawable-mdpi/window_logo_wo_logo.png res/drawable-mdpi/window_pass.png res/drawable-mdpi/ymk_balloon_black.9.png res/drawable-xhdpi/amex.png res/drawable-xhdpi/back.png res/drawable-xhdpi/btn_c.png res/drawable-xhdpi/btn_n.png res/drawable-xhdpi/cirrus.png res/drawable-xhdpi/disc.png res/drawable-xhdpi/fbi.png res/drawable-xhdpi/field.png res/drawable-xhdpi/ic_launcher.png res/drawable-xhdpi/mastercard.png res/drawable-xhdpi/number_text.png res/drawable-xhdpi/number_text_tap.png res/drawable-xhdpi/progress_bg_holo_light.9.png res/drawable-xhdpi/progress_primary_holo_light.9.png res/drawable-xhdpi/tab_selected_focused_holo.9.png res/drawable-xhdpi/tab_selected_holo.9.png res/drawable-xhdpi/tab_selected_pressed_holo.9.png res/drawable-xhdpi/tab_unselected_focused_holo.9.png res/drawable-xhdpi/tab_unselected_holo.9.png res/drawable-xhdpi/tab_unselected_pressed_holo.9.png res/drawable-xhdpi/visa.png res/drawable-xxhdpi/back.png res/drawable-xxhdpi/ic_launcher.png classes.dex META-INF/MANIFEST.MF META-INF/CERT.SF META-INF/CERT.RSA
Permissions required by the malware:
- Permission to send SMS
- Permission to receive SMS
- Permission to call a phone number
- READ_CONTACTS
- READ_LOGS
- CHANGE_WIFI_STATE
- INTERNET
- BIND_DEVICE_ADMIN
The malware implements a device administration component, and may thus be more difficult to delete from the handset.
The malware connects to Internet.
It contacts the following URLs:
- hxxp://XXXXX.10/french/gate.php
- hxxp://XXXXX.com.
- hxxp://XXXXXe.com/
- hxxp://XXXXXiz
Certificate information:
Owner : CN=Alex Rothshield OU=IT O=Adobe LTD. L=Toronto ST=Canada C=CA
Serial number: 7aa968dc
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |