Riskware/SAppLock!Android
 Analysis
Analysis
Riskware/SAppLock!Android is a riskware that targets Android devices.
This application is detected because it can be used by an attacker against a victim in the following circumstances:
- Remote lock. An attacker can use the riskware to lock a victim's device. Locking the device can be done remotely by SMS.
- Malware hiding. The riskware has the intriguing capability to have given applications act as if they had crashed. Typically, an attacker could install a malware or a spyware on the victim's phone and 'protect' it with the riskware. Whenever the victim would try to launch the malware/spyware, a notification would pop up and say the application has crashed, and some victims would certainly believe this is merely a bug. In reality, the malware/spyware would be running perfectly well on the phone.
- Collecting pictures. An attacker could use the riskware to get an up-to-date picture of the victim. Indeed, the riskware takes pictures with the front camera whenever an end-user fails to unlock an application protected by password. Thus, the attacker with physical access to the mobile phone could intentionally lock an important application on the phone and get pictures of whoever tries to use the app
The main features of the application is the Lock Screen Protection and the App Protection. With the application, you can put other apps in 3 different categories (AppLock, Screen and Rotation):
- App Lock. Apps in the category 'AppLock' need a password to be launched or act like they are not working anymore (fake lock).
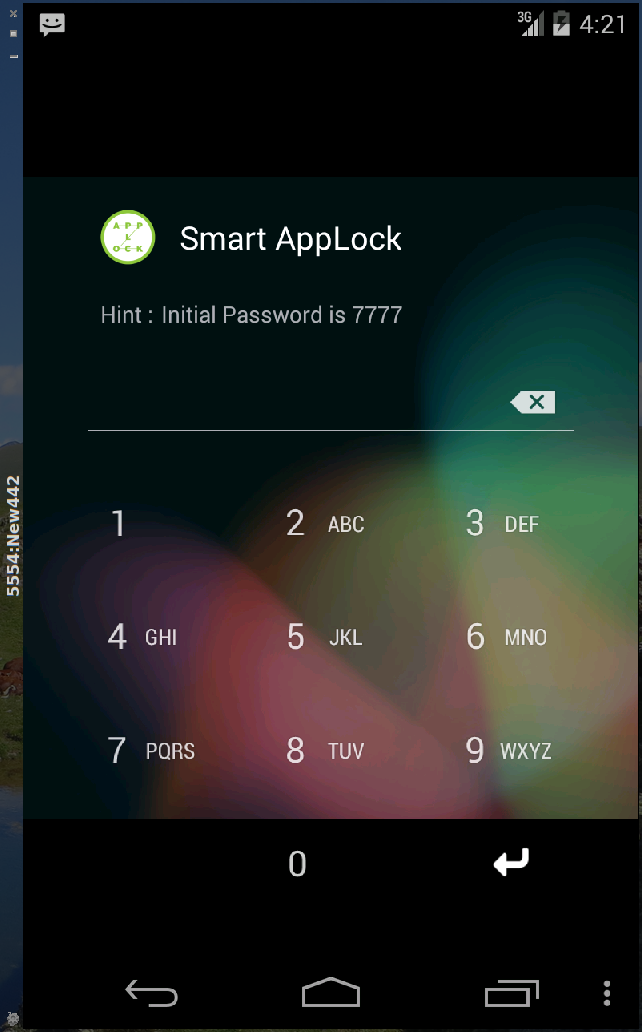
Legend. Application lock
- Screen. Apps in the category 'Screen' will never turn off the screen during execution (for instance for ebook reader).
- And apps in the category 'Rotation' will never auto-rotate (landscape/portrait) during execution.
If a user fails to login a picture from the frontcamera is saved on the SD card of the device.
Technical Details
The riskware comes packaged as com.sp.protector.free. Its main activity is ProtectorApplication. The app runs a service (com/sp/protector/free/engine/SAPServiceKernel) which is permanently checking the current top running task. When an application is launched it will get the top running task (com/sp/protector/free/engine/co.class) and the service is checking if this app was put into the list of locked applications (com/sp/protector/free/k.class). If it is the case it removes any pending posts of callbacks and sent messages whose this application is token (com/sp/protector/free/i.class) and starts the password form (or fake stopped running (com/sp/protector/free/engine/o.class.l())) on the screen and just contiues it if the entered password was correct.
The storage of the pictures of the failed login can be found on the SD card of the device:
Environment.getExternalStorageDirectory() + "/smart app protector" + "/obs" + integer + "#" + 1;
The SMS receiver for the remote lock is located in com/sp/protector/free/receiver/SMSReceiver. The default keyword for to lock the screen is "@protect".
If the user wants to uninstall the application he needs to go to SETTINGS->Location and Security-> Device Administrator and deselect the admin for the application.
The riskware uses several external SDKs such as Cauly, TriD, InMobi... The malware asks for the following permissions:
com.android.vending.BILLING GET_ACCOUNTS EXPAND_STATUS_BAR ACCESS_NETWORK_STATE ACCESS_WIFI_STATE CALL_PHONE RECEIVE_SMS READ_PHONE_STATE PROCESS_OUTGOING_CALLS CHANGE_WIFI_STATE WAKE_LOCK GET_TASKS WRITE_SETTINGS READ_LOGS INTERNET DISABLE_KEYGUARD VIBRATE WRITE_EXTERNAL_STORAGE RECEIVE_BOOT_COMPLETED CAMERA RECORD_AUDIO BLUETOOTH BLUETOOTH_ADMIN CHANGE_NETWORK_STATE ODIFY_PHONE_STATE SYSTEM_ALERT_WINDOW com.android.launcher.permission.INSTALL_SHORTCUT USE_CREDENTIALSThe riskware is signed with this certificate:
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 1283157080 (0x4c7b6c58)
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=ko, L=Incheon, CN=Young-Hak Jung
Validity
Not Before: Aug 30 08:31:20 2010 GMT
Not After : Aug 17 08:31:20 2060 GMT
Subject: C=ko, L=Incheon, CN=Young-Hak Jung
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
...
This riskware was first detected by SherlockDroid, using Alligator and analyzed by Isa Fredriksen and Marc-Andre Baer, under the supervision of Ludovic Apvrille (Telecom ParisTech) and Axelle Apvrille (Fortinet).
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.