JS/Nemucod.DLM!tr.dldr
 Analysis
Analysis
JS/Nemucod.DLM!tr.dldr is a generic detection for a Javascript Downloader Trojan for a Ransomware. Since this is a generic detection, malware that are detected as JS/Nemucod.DLM!tr.dldr may have varying behaviour.
Below are examples of some of its behaviours:
- This malware drops the following file(s):
- undefinedInternet_Cacheundefined\counter[1].js : This file is detected as JS/Nemucod.9F86!tr.
- undefinedTempundefined\[Random].php : This file is detected as PHP/Agent.1834!tr.
- undefinedTempundefined\[Random].exe : This file is non-malicious PHP component.
- undefinedTempundefined\php5.dll : This file is non-malicious PHP component.
- undefinedTempundefined\[Random].doc : This file is non-malicious data file.
- This malware attempts to connect to the following sites:
- 21{Removed}.186.33.19
- 5{Removed}.251.149.184
- 4{Removed}.40.164.137
- 4{Removed}.40.165.35
- 8{Removed}.76.20.10
- northernhydr{Removed}.co.uk
- newbor{Removed}.cm
- kamin{Removed}.ru
- bombayhospitalandtraumacentr{Removed}.com
- 8{Removed}.93.88.22
- m{Removed}.bora.beget.ru
- rcproracin{Removed}.com
- malta234{Removed}.startdedicated.com
- Based on our samples, this malware disguises itself as zipped archive UPS Parcel document and on a typical user setup this malware may cause to display the following prompts:
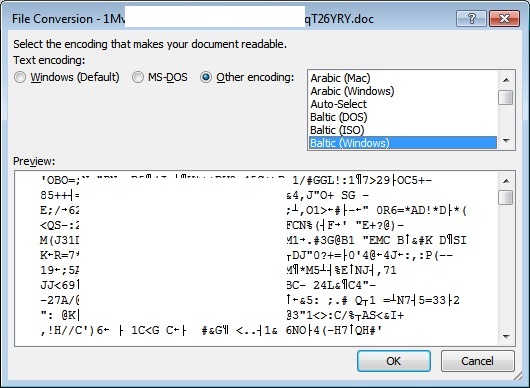
- Figure 1: Data file being opened as Document.
- This malware has Ransomware capabilities and is exhibited by the Ransom note below:
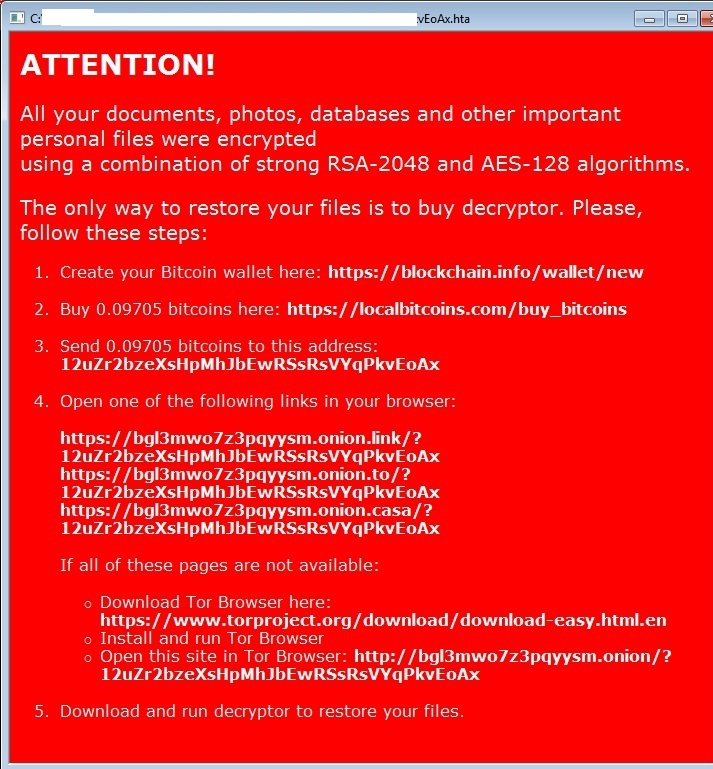
- Figure 2: Ransomware notes.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |