 Analysis
Analysis
JS/Coinminer.SX!tr is a generic detection for a Javascript coinminer. Since this is a generic detection, malware that are detected as JS/Coinminer.SX!tr may have varying behaviour.
Below are examples of some of these behaviours:
- Uses the following JSON object "CoinHive.CONFIG" as configuration information:
- LIB_URL: hxxps://coinhiv{Removed}.com/lib/
- ASMJS_NAME : worker-asmjs.min.js : This is possibly the hashing library
- REQUIRES_AUTH : false
- WEBSOCKET_SHARDS : [Array of URLs] wss://ws[3DIGITS].coinhive.com/proxy
- CAPTCHA_URL : hxxps://coinhiv{Removed}.com/captcha/
- MINER_URL : hxxps://coinhiv{Removed}.com/media/miner.html
- AUTH_URL : hxxps://authedmin{Removed}.com/authenticate.html
- Checks for to see if the browser has WASM support. Otherwise will attempt to use ASMJS. It is likely that one of these modules contain the hashing algorithm.
- Creates a "job thread" to perform the hashing, which makes use of the Cryptonight hashing algorithm.
- The hashing algorithm may be called "CRYPTONIGHT_WORKER_BLOB" and looks as the following:
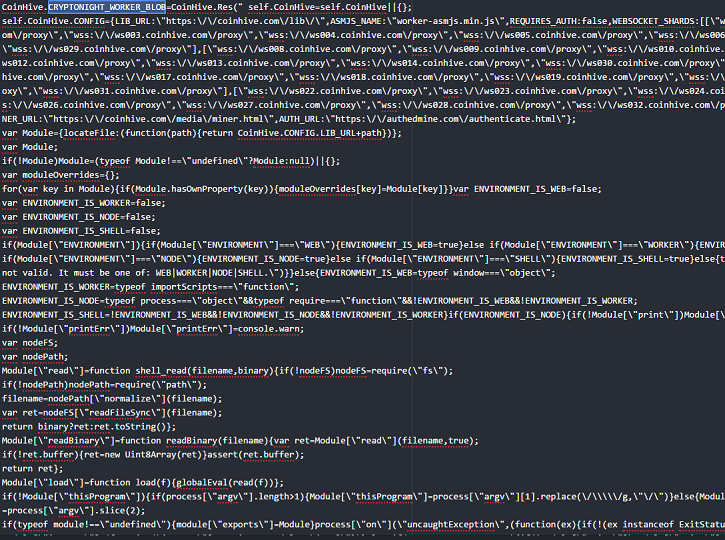
- Figure 1: The beginning of the worker algorithm.
|
 Analysis
Analysis
 Recommended Action
Recommended Action Telemetry
Telemetry