W64/Ryuk.223E!tr.ransom
 Analysis
Analysis
W64/Ryuk.223E!tr.ransom is a generic detection for a Ransomware Ryuk trojan. Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- %SystemDrive%\Users\Public\sys : This file is non-malicious data file .
- %SystemDrive%\Users\Public\public : This file contains the RSA public key for the purpose of encryption.
- %SystemDrive%\Users\Public\unique_id_do_not_remove : This file contains the hardcoded key for the purpose of encryption.
- %SystemDrive%\Users\Public\window.bat : This bat file deletes the shadow volume copies and other backup files so that the user cannot restore them.
- ryukreadme.txt/RyukReadMe.txt : This text file is dropped in every infected folder and will serve as ransom notes.
- This Ransomware either uses the filenaming format {original name.ext}.RYK or does not change the name or extensions of the files that are being encrypted.
- This Ransomware attempts to inject its code to the address space of all others processes except explorer.exe, csrss.exe, lsaas.exe.
- Affected victims of this Ransomware are redirected by the attacker via:
- JohnFraz@protonmail.com
- JohnFraz@tutanota.com
- ibfosontsing@protonmail.com
- ibfosontsing@tutanota.com
- kbkj@tutanota.com
- kjhkj@protonmail.com
- AlanParkerre33@tutanota.com
- AlanParkerre33@protonmail.com
- fabonmissreal1971@protonamail.com
- AlconFetcher@tutanota.com
- FionaBates90@protonmail.com
- FionaBates90@tutanota.com
- DejackomeAjna@protonmail.com
- ElmersVictoria@tutanota.com
- This malware was also observed to affect/encrypt files located on shared drive within the same subnet.
- This malware may apply any of the following registry modification(s):
- HKCU\Software\Microsoft\Windows\Currentversion\Run
- Svchos = %currentfile%
- HKCU\Software\Microsoft\Windows\Currentversion\Run
- This Ransomware kills processes related to antivirus, database, document editing software and backup.
- The attacker runs the commandline scripts to perform the following tasks:
- To gain persistence by adding itself to the autorun registry entry.
- Below is an illustration of the malware's Ransom notes:
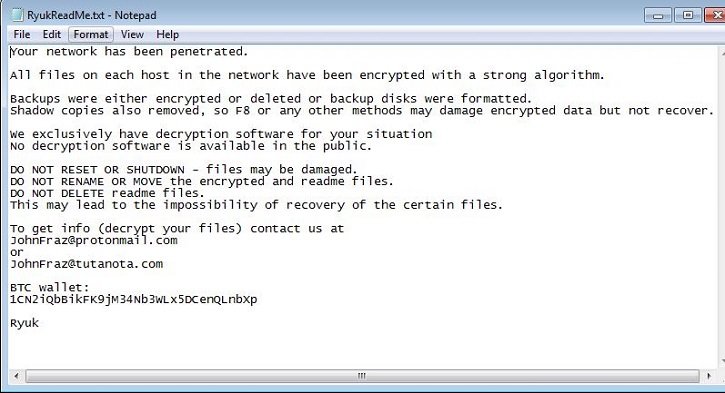
- Figure 1: Ransom Notes.
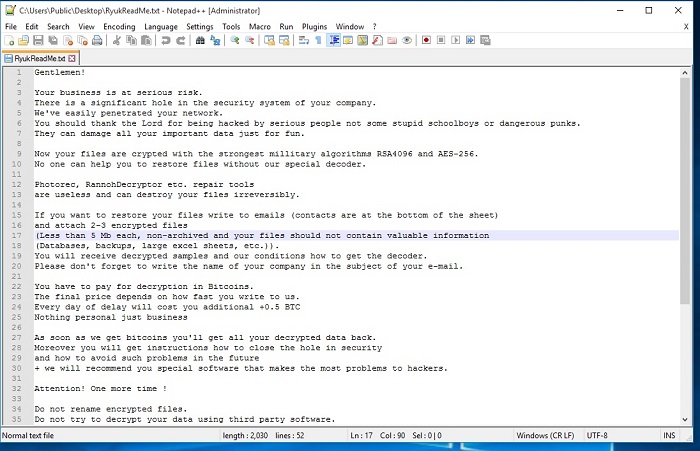
- Figure 2: Ransom Notes variation.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |
Version Updates
| Date | Version | Detail |
|---|---|---|
| 2022-01-11 | 89.08603 | |
| 2019-12-05 | 73.58000 | Sig Updated |
| 2019-11-12 | 73.02100 | Sig Updated |
| 2019-05-21 | 68.68100 | Sig Updated |
| 2019-04-23 | 68.01800 | Sig Updated |
| 2019-02-19 | 66.50100 | Sig Updated |
| 2018-12-07 | 64.73000 | Sig Updated |
| 2018-12-06 | 64.70200 | Sig Updated |
| 2018-11-21 | 64.34900 | Sig Updated |
| 2018-11-21 | 64.34800 | Sig Updated |