MSIL/BlackRuby.CC3E!tr.ransom
 Analysis
Analysis
MSIL/BlackRuby.CC3E!tr.ransom is a detection for a Black Ruby Ransomware trojan.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- HOW-TO-DECRYPT-FILES.txt: This file is a txt file and will serve as ransom notes. It will be dropped in every affected folder.
- Affected files of this Ransomware will use the prepending filenaming format as Encrypted_{Random}.BlackRubyLight.
- This malware was also observed to affect/encrypt files located on shared drive within the same subnet.
- After executing this malware, it may delete itself.
- The malware will try to download strings from the following url, but this url has already been removed.
- hxxp://geoip.nek{Removed}.com/api
- Below is a sample illustration of the Ransom notes:
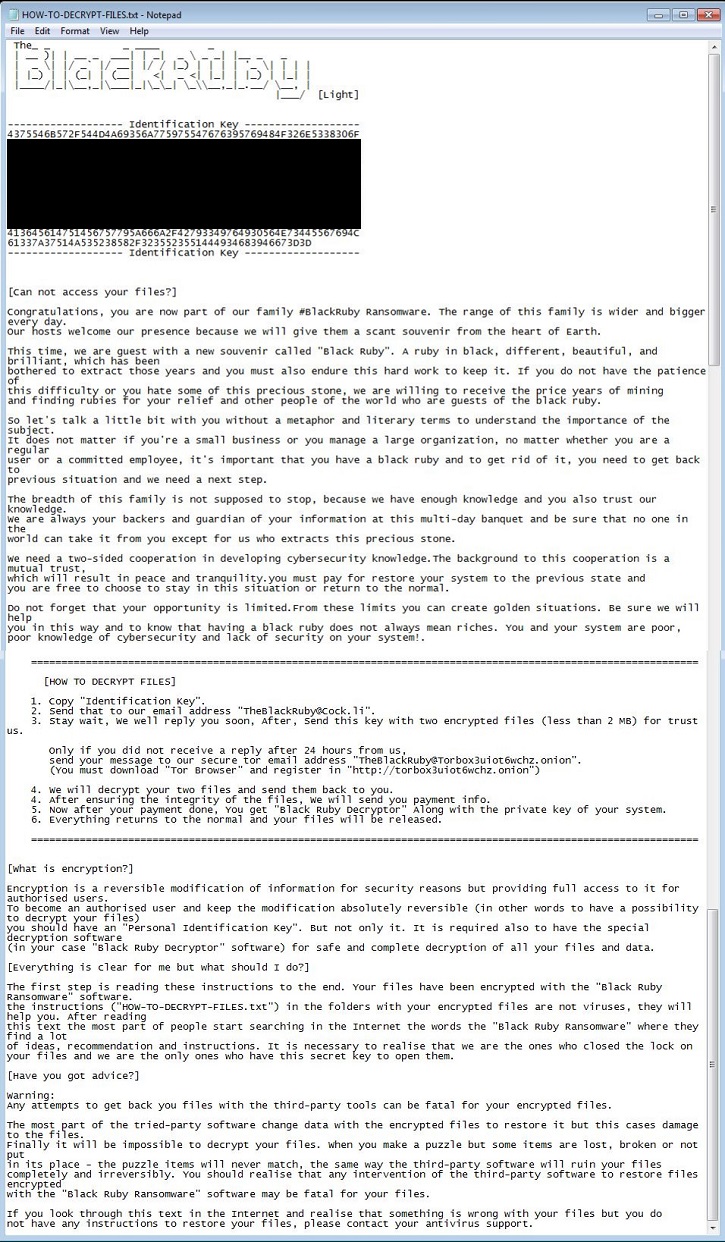
- Figure 1: Ransom notes.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |