SymbOS/Comwar.3.0!worm
 Analysis
Analysis
This memory resident Symbian malware arrives as a SIS package or Symbian installer file. It is capable of spreading via Bluetooth and Multimedia Message Service (MMS) messages.
Installation of the malware
The SIS package installs the malware as a system process to hide it from some process viewing tools. It creates a copy of itself in the root folder of the flash drive using a randomly generated filename. It also drops another copy of itself in the libs directory of the system folder in the flash drive and any attached MMC drives:
- undefinedEPOCROOTundefined\undefinedRANDOM_NAMEundefined.exe (60,792 Bytes)
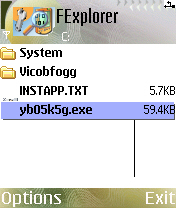
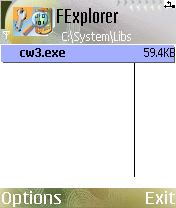
- undefinedEPOCROOTundefined\system\libs\cw3.exe (60,792 Bytes)
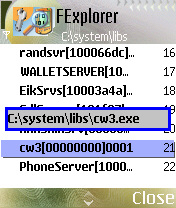
Below is a screenshot of the protected malware process cw3, as viewed using a third party tool:
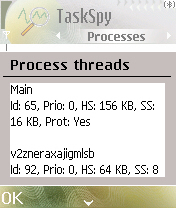
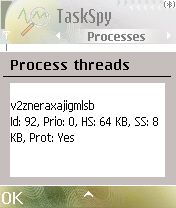
The malware process also creates a protected thread with a randomly generated name, such as the one showed in the screenshot that follows:
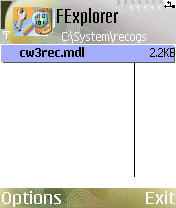
In addition, this symbian malware also creates the following MDL recognizer file to allow automatic execution of the malware:
- undefinedEPOCROOTundefined\system\recogs\cw3rec.mdl (2,284 Bytes)
Propagation via Bluetooth
To spread via Bluetooth, the virus seeks phones nearby that have the Bluetooth protocol enabled. The virus then attempts to send itself as a SIS file with a randomly generated name to every device found.
The recipient will first notice a request to receive a program and the message may be similar to the one below:
Receive message via Bluetooth from undefinedphone modelundefined? Yes
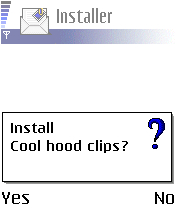
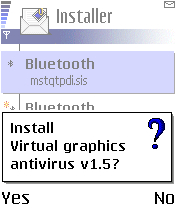
Once the user clicks YES, it will be followed by a prompt asking the user to install an application. Some application names utilized by the malware to disguise itself are the following:
- Cool hood clips
- Final Document v1.5
- Final Images
- Nice memory manager
- Trend micro mail recorder v5.7
- Virtual graphics antivirus v1.5
Here are sample screenshots of the installation prompts that shows the application names used by the malware:
Here is a screenshot of an Inbox folder containing the random named SIS packages sent by the malware via Bluetooth:
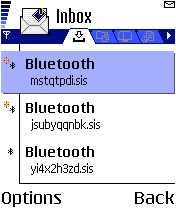
The virus is persistent such that even after pressing "No" to the installation prompt, multiple Bluetooth transfer requests would still be received. The barrage of requests could prove to be too many and quite annoying to mobile device owners receiving the request. The user could subsequently give in and allow the virus to be received and installed, thus infecting the device.
Propagation via MMS
To spread via MMS, this malware browses the infected phone's address book and sends an MMS message containing a copy of the malware to any of the listed contacts. Moreover, any outgoing Short Message Service (SMS) or MMS messages sent by the user of the infected phone may be followed by an infected MMS message sent by the malware without the user's knowledge.
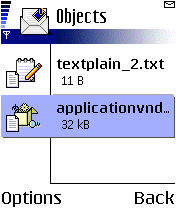
The infected MMS message contains either of the following:
- One application object containing an installer for the EPOC malware.
- Two objects, where one is a normal text file while the other is an application object containing an installer for the EPOC malware.
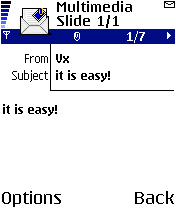
The following is an example of the contents of a normal text file included in an MMS message sent by the malware:
Other Payloads
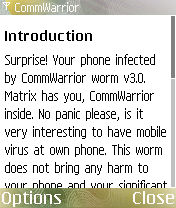
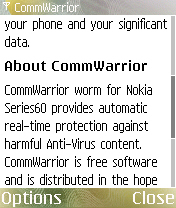
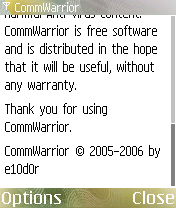
After a while, this malware drops the following HTML page and displays it using the default browser application:
- undefinedEPOCROOTundefined\system\libs\cwinfo.html (738 Bytes)
 Recommended Action
Recommended Action
- Kill the malware process named cw3.
- Delete all modules related to this virus from the flash and MMC drives of the infected device:
- undefinedEPOCROOTundefined\undefinedRANDOM_NAMEundefined.exe (60,792 Bytes)
- undefinedEPOCROOTundefined\system\libs\cw3.exe (60,792 Bytes)
- undefinedEPOCROOTundefined\system\libs\cwinfo.html (738 Bytes)
- undefinedEPOCROOTundefined\system\recogs\cw3rec.mdl (2,284 Bytes)