Android/Spywaller.A!tr
 Analysis
Analysis
Android/Spywaller.A!tr is a piece of malware targetting Android mobile phones.
The malicious package comes disguised as an application called 'Google Service'. Its main job is to decrypt and load the malicious package hidden within it.
The malicious package is a comprehensive package that can perform functions starting from collecting data (like Contact information, location, SMS messages, the list of installed applications, message histories from various messengers such as WhatsApp, Viber, Skype, BBM etc.) to monitoring received SMS messages and calls, record audio from the phone and incoming calls, take pictures and record video from the infected phone etc.
It can even be made to perform functions like drain the phone's battery, slow down operation, switch to Flight Mode, send Fake Messages to the victim and even delete itself.
The main application is called "Google Service"(Fig1) and comes in the package "com.schemedroid".

Fig1 :
It launches a MainActivity that in turn launches the service SchemeService that performs the following functions :
- It reads and decrypts (XOR with 0xff) a file misleadingly named 'droid.png' in the package assets
- The decrypted file is saved as annotation.jar and it's classes are loaded using the DexClassLoader API loadClass()
- The names of classes loaded are present in the code in Base64 encoded form. These classes are 'com.GoogleService.MainService' and 'com.GoogleService.Common.Config' (described below)
- assets/logo.png = Root exploit for SDK versions 14 to 18
- assets/help4.png = Root exploit for other SDK versions
- assets/splash = Superuser 'su' binary
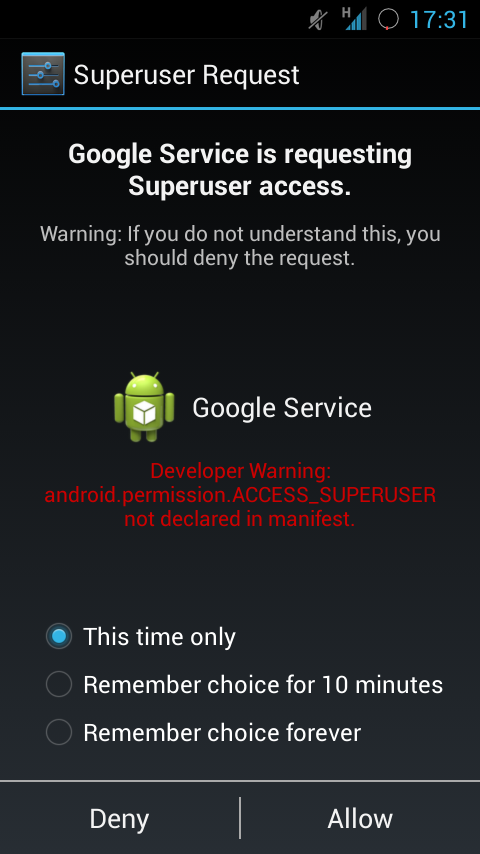
Fig2 :
com.GoogleService.MainService
This service collects various data from the infected phone and sends it to an attacker's server whose address is contained within an encrypted file 'setting.prop' in the package assets.
It also blocks any traffic from applications with package names "com.qihoo360.mobilesafe" and "com.qihoo.antivirus" (corresponding to a Chinese Anti-Virus). It establishes this by dropping binaries for busybox and iptables and setting up filtering rules to block those applications by their UID.
It collects the following data from the phone :
- getAppList() - The list of installed packages on the phone
- getSMS() - The SMS messages on the phone are read, encrypted and stored in the files sys105.ini (for received SMS), sys109.ini (for sent SMS) and sys107.ini (for other messages).
- getQQ() - The 'databases' and 'shared_prefs' folders corresponding to the Tencent QQ messenger application are zipped and saved to the /tmp folder under a file with the QQ messenger package name Similarly, the following folders for the corresponding applications are zipped and saved.
- getWechat() - Folders 'MicroMsg' and 'shared_prefs' for the WeChat messenger.
- getSkype() - TFolder 'files' for the Skype Android application.
- getWhatsApp() - Folders 'databases' and 'shared_prefs' for WhatsApp.
- getVoxer() - Folder 'databases' for Voxer.
- getTalkbox() - Folders 'databases' and 'files' for Talkbox.
- getCoco() - Folder 'databses' for the Coco messenger.
- getViber() - Folders 'databases' and 'files' for the Viber messenger.
- getZello() - Folder 'shared_prefs' for 'Zello'
- getOovoo() - Folder 'databases' for 'Oovoo'
- getBbm() - Folders 'files' and 'shared_prefs' for the Blackberry Messenger on Android.
- RecorderReceiver - Records audio from the victim's phone when instructed.
- GpsReceiver - Toggles the GpsListener state on the phone to track a user's location.
- CameraReceiver - Takes pictures or records videos from the infected phone camera when instructed.
- ContactObesrver - Monitors any changes in phone contacts.
- SMSReceiver - Monitors incoming SMS messages on infected phone.
- PhoneReceiver - Records phone numbers of all outgoing calls.
- RadioObserver - Records the audio for all incoming calls.
- SdCardReceiver - Monitors changes in the SDCard i.e. when it is mounted and ejected.
- An observer to monitor when the SIM card on the phone is changed.
- sys103.ini for collected SMS messages
- sys118.ini for the list of installed application
- sys200.ini and sys201.ini for received calls information
- sys202.ini for recorded audio
- sys205.ini for collected MMS messages etc.
- Drain battery on the phone by performing several miscellaneous operations like toggling GPS, repeated connection to internet URLs etc.
- Switch the phone to flight mode.
- Slow down performance of the phone by performing miscellaneous operations in the background.
- Look for particular files on the phone and send it back to the C&C.
- Get a list of all audio and video files (with common extensions) on the phone.
- Display a fake SMS in the victim's Inbox with a specific sender and message. The sendText() API call is obscured using Java Reflection.
- Decrypt and launch a daemon on the phone disguised as 'about.png' in the package assets.
- Delete itself.
Permissions required by the application:
- WRITE_APN_SETTINGS
- SET_DEBUG_APP
- RECEIVE_BOOT_COMPLETED
- KILL_BACKGROUND_PROCESSES
- RECORD_AUDIO
- RECORD_VIDEO
- WRITE_SETTINGS
- WRITE_SECURE_SETTINGS
- CALL_PHONE
- PROCESS_OUTGOING_CALLS
- READ_CONTACTS
- WRITE_CONTACTS
- RECEIVE_SMS
- RECEIVE_MMS
- RECEIVE_WAP_PUSH
- INTERNET
- SEND_SMS
- READ_SMS
- WRITE_SMS
- ACCESS_NETWORK_STATE
- READ_PHONE_STATE
- MODIFY_PHONE_STATE
- MODIFY_AUDIO_SETTINGS
- VIBRATE
- CHANGE_NETWORK_STATE
- WRITE_EXTERNAL_STORAGE
- RESTART_PACKAGES
- READ_LOGS
- ACCESS_COARSE_LOCATION
- ACCESS_FINE_LOCATION
- WAKE_LOCK
- CHANGE_WIFI_STATE
- READ_HISTORY_BOOKMARKS
- ACCESS_WIFI_STATE
- READ_CALL_LOG
- CAMERA
- SYSTEM_ALERT_WINDOW
Aimed at Chinese users
Certificate information:
- Owner: CN=w, OU=w, O=localhost, L=w, ST=w, C=CN
- Issuer: CN=w, OU=w, O=localhost, L=w, ST=w, C=CN
- Serial number: 55f0ebf4
- Valid from: Thu Sep 10 04:33:24 CEST 2015 until: Fri Jun 13 04:33:24 CEST 2070
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.