JS/Nemucod.BIF!tr.dldr
 Analysis
Analysis
JS/Nemucod.BIF!tr.dldr is a generic detection for a trojan. Since this is a generic detection, malware that are detected as JS/Nemucod.BIF!tr.dldr may have varying behaviour.
Below are examples of some of these behaviours:
- This malware also issues a PowerShell command line that downloads hxxp://thereupo{Removed}.top/user.php?f=3.dat as undefinedAppDataundefined\Roaming.exe then later on executes it. However, this URL was offline at the time of this analysis. Some instances of this malware were observed to use the URL location hxxp://my.Internaldati{Removed}.ru/js/boxun4.bin, which also yielded no result. Considering the recent trend of JS downloaders during the time of analysis, it is highly possible that the intended downloaded file is a ransomware.
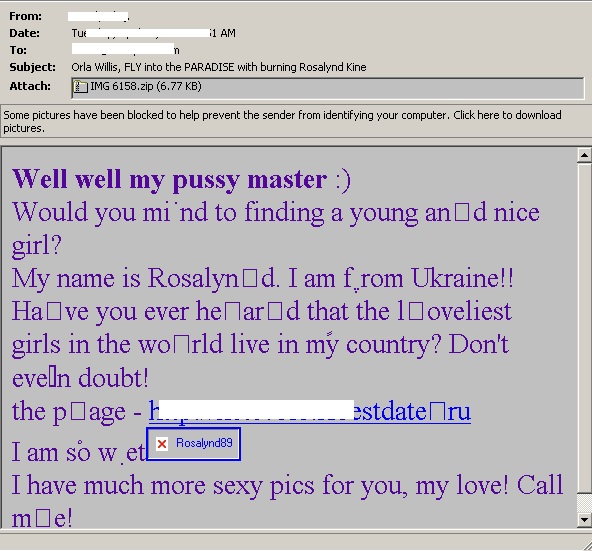
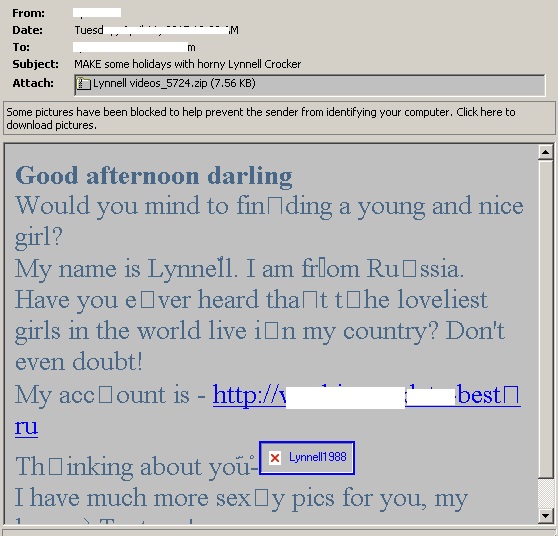
- This Javascript downloader appears to have been delivered through a spam campaign arriving as a ZIP attachment. Below are examples of some of these spam emails:
- Figure 1: Spam email.
- Figure 2: Spam email.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |