W32/Petya.EOB!tr
 Analysis
Analysis
W32/Petya.EOB!tr is a generic detection for a type of ransomware that encrypts files on the victim's computer. Since this is a generic detection, files that are detected as W32/Petya.EOB!tr may have varying behavior.
Below are examples of some of these behaviors:
- This malware arrives as a DLL. The malicious actions can be found in the DLL's first exported function.
- It checks if there is a file in the C:\Windows folder that has the same name as itself (with no extension name). For example, if the malware is executing as Petya.dll, it checks if the file C:\Windows\Petya exists. If the file can be found, it exits. If not, it proceeds with the rest of its actions.
- It overwrites the Master Boot Record and encrypts the disk.
- In order to encrypt disk, it will schedule a restart/shutdown using these commands:
- cmd.exe "%WINDIR%\system32\shutdown.exe /r /f"
- schtasks.exe " /TR "%WINDIR%\system32\shutdown.exe /r /f" /ST {HH:MM}
- Upon reboot, it displays a fake Chkdsk message that it is "Repairing file system on C:". However, it is likely already using this time to encrypt the victim's disk.
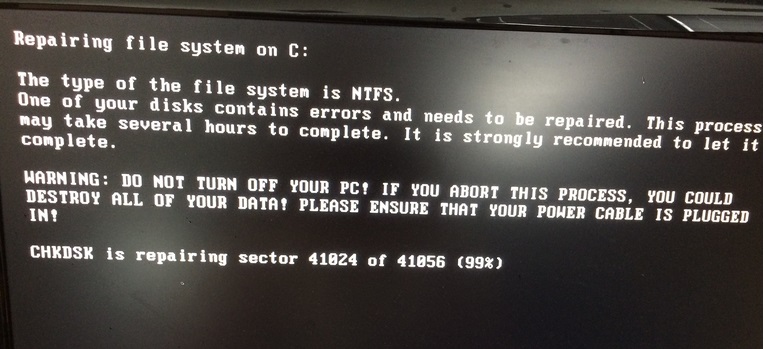
- Figure 1: Boot Chkdsk message.
- Files with extension names commonly associated with data files are targeted for encryption, such as:
- .3ds
- .7z
- .asp
- .doc
- .msg
- .ova
- .xls
- Once this progress prompt is complete, it displays a a ransom message on the screen stating that the victim's files are encrypted and in order to use their decryption, the victim needs to send $300 worth of Bitcoins to this address: 1Mz7153H{Removed}AtNbBWX.
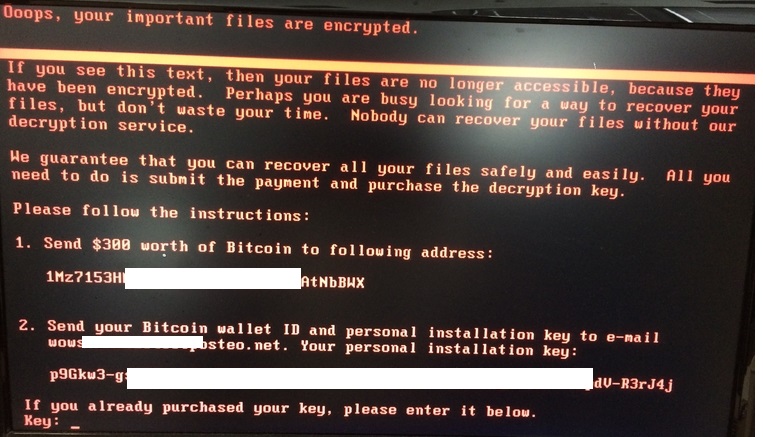
- Figure 2: Ransom message.
- It drops a file [Random].tmp in the Temporary folder, then runs it. This file is the Mimikatz tool which is used to gain access to logged on users and their passwords. The malware uses a named pipe to communicate with it.
- It drops the file dllhost.dat to the Windows folder. This is the PsExec tool.
- There are indications that the EternalBlue exploit is used to spread this malware onto unpatched machines within the victim's network.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |