JS/Nemucod.DRC!tr
 Analysis
Analysis
JS/Nemucod.DRC!tr is a generic detection for a JS Downloader trojan. Since this is a generic detection, malware that are detected as JS/Nemucod.DRC!tr may have varying behaviour.
Below are examples of some of these behaviours:
- This malware spawns a powershell command line that intends to download from hxxps://aedward{Removed}.co/wp-includes/IXR/get.php? and drop it as undefinedAppDataundefined\[Random].exe, afterwhich it is executed. During the time of our tests the URL appears to be offline.
- This malware is usually embedded within Word documents, below are some examples of infected document and infected mail:
- Figure 1: Infected Document.
- Figure 2: Infected document.
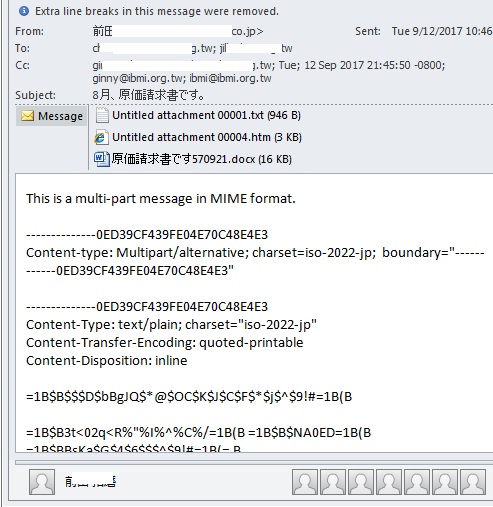
- Figure 3: Email with Infected Document.
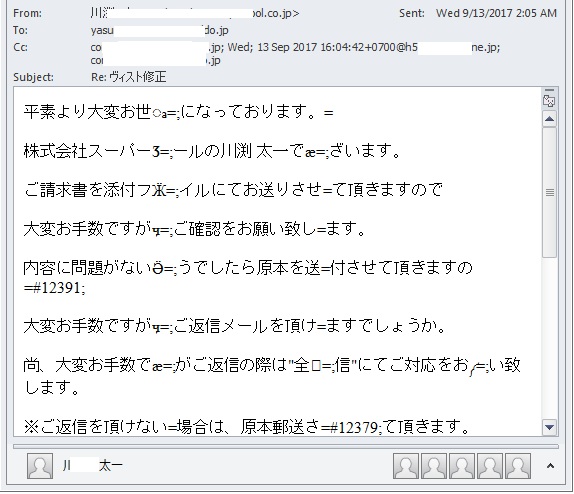
- Figure 4: Infected email.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |