W32/Injector.DSOV!tr
 Analysis
Analysis
W32/Injector.DVOS!tr is a generic detection for a downloader trojan.
Since this is a generic detection, this malware may have varying behaviour.
Below are some of the observed characteristics/behaviours:
- This malware has observed to attempt to connect to the following websites:
- http://hk{Removed}.kr
- http://mkhydraul{Removed}.rs
- http://khurshide{Removed}.com
- http://popcornki{Removed}.net
- http://ud{Removed}.com.pk
- http://equipmesolutio{Removed}.com
- If connection is succssful, it may attempt to download an executable with the path:
- http://[Url]/[RandomName_1]/Panel/[RandomName_1].exe
- Figure 1: Subdirectory on a hacked site.
- This malware may also delete itself after running.
- This malware has been found to be linked to the Fareit (aka Pony), a widely-distributed password stealer trojan.
- This malware attempted to download another component and during our tests we suspect that this component is a Fareit compiled binary with specific configurations.
- Certain hacked websites have been found to contain the original Fareit Panel and archive
- The following list of files were found to be associated with the panel (MD5 hash may vary):
- admin.php - MD5: c8c64af651c2f07bd2620666aa7317c4
- config.php - MD5: 98b147282e545e613764e971bfe74e93
- gate.php - MD5: f908c85c5566865264d9e0520c18d934
- redirect.php - MD5: f9d6f68eec8ebab0de57bfe7bd093170
- setup.php - MD5: 367bf2d341315af743389f79952707c1
- includes/
- chart.php - MD5: c841bcb49990805f5ea70c5c99ea818a
- database.php - MD5: 5ef1f7d259f02ba5a9e3847c32cb7eca
- lang.php - MD5: c56fd29cb1bd65697f4b392856bed829
- misc.php - MD5: 93a1b7cb8d4172e93533617e26ae5dda
- password_modules.php - MD5: 13a030e5de70cef5c803b3cec1d3438f
- The files can be seen in the panel as:
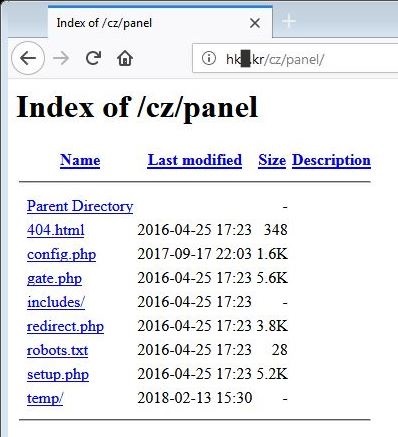
- Figure 2: Panel.
The following image shows a website that has been hacked with the path "cz" added:
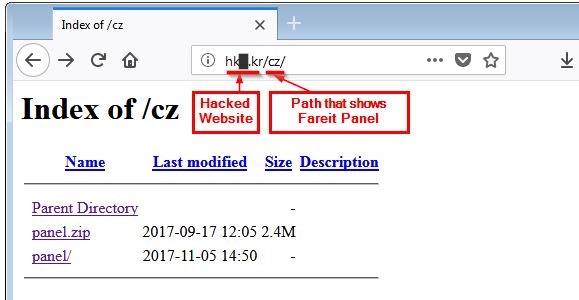
|
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |