 Analysis
Analysis
W32/GandCrab.FOD!tr.ransom is a generic detection for a Ransomware GANDCRAB trojan. Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
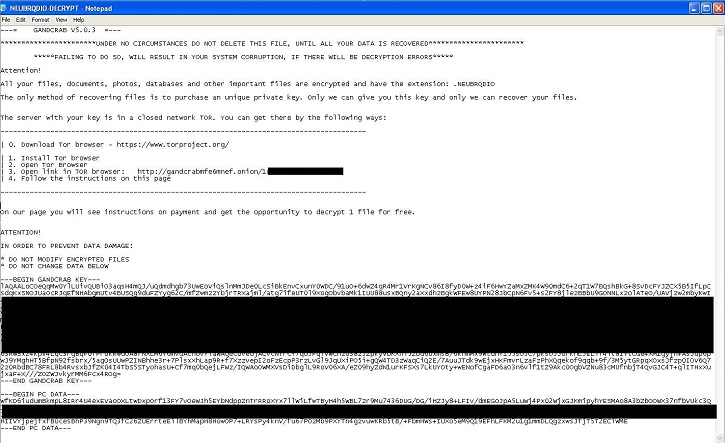
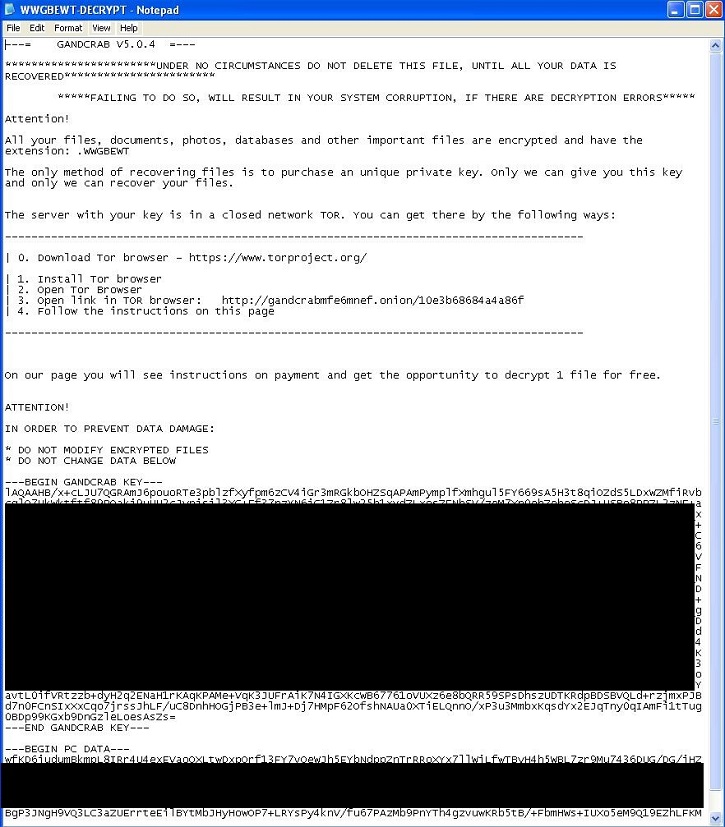
- XXXXX-DECRYPT.txt : This file is txt file and will serve as ransom notes, where X is alphanumeric character.
- XXXXXXXXX-DECRYPT.txt : This file is txt file and will serve as ransom notes, where X is alphanumeric character.
- XXXXXXX-DECRYPT.txt : This file is txt file and will serve as ransom notes, where X is alphanumeric character.
- XXXXXXXXXX-DECRYPT.txt : This file is txt file and will serve as ransom notes, where X is alphanumeric character.
- XXXXX-DECRYPT.html: This file is html file and will serve as ransom notes, where X is alphanumeric character..
- XXXXXXXX-DECRYPT.txt : This file is txt file and will serve as ransom notes, where X is alphanumeric character.
- XXXXXXXXXX-MANUAL.txt : This file is txt file and will serve as ransom notes, where X is alphanumeric character.
- %AppData%\cexplorer.exe: One variant of this malware drops this file. This file is currently analyzed as none malicious.
- %AppData%\update.exe : One variant of this malware drops this file. This file is detected as W32/GandCrab.FOD!tr.ransom.
- %Temp%\xxxx.tmp.exe : This file is currently detected as W32/GandCrab_V5_0_4!tr.ransom.. Here x is any aphanumeric character.
- %Appdata%\DriverHD.exe : One variant of this malware drops this file. This file is detected as W32/GandCrab_V5_0_4!tr.ransom.
- Affected files of this Ransomware may use any of the following filenaming format:
- [OriginalFileName].xxxxx
- [OriginalFileName].xxxxxxxxx
- [OriginalFileName].xxxxxxx
- [OriginalFileName].xxxxxxxx
- [OriginalFileName].xxxxxxxxxx
where x is alphanumeric character.
- This malware was also observed to affect/encrypt files located on shared drived within the same subnet.
- This Ransomware also changes desktop background to ransom notes.
- One variant of this malware apply may apply following registry modification(s) :
- HKLM\Software\Microsoft\Windows\Currentversion\Run
- chameleon explorer = "program files\chameleon explorer\chameleonexplorer.exe\" /startup
This automatically executes the dropped file every time any user logs on to the infected system.
- One variant of this malware runs the command line operations to perform following tasks:
- To make the installation of the chameleon explorer silent.
- To replace the file explorer by chameleon exploer.
- This malware may connect to any of the following remote sites(s):
- 88.99.66.3{Removed}
- zsn5qtrgfpu4tmpg.tor2{Removed}.blutmagie.de
- hxxp://www.billeri{Removed}.com
- hxxp://www.macarte{Removed}.eu
- hxxp://www.poke{Removed}.com
- hxxp://perova{Removed}.ru
- hxxp://asl-{Removed}.ru
- hxxp://www.fabb{Removed}.gm
- hxxp://www.perfectfunnel{Removed}.com
- hxxp://www.wash-{Removed}.com
- hxxp://al{Removed}.be
- hxxp://ce{Removed}.net
- hxxp://www.n2{Removed}.co.th
- hxxp://www.rm{Removed}.in
- hxxp://boatshow{Removed}.com
- hxxp://dna-{Removed}.com
- hxxp://ac{Removed}.fr
- www.haar{Removed}.biz
- www.2mmot{Removed}.biz
- www.eyho{Removed}.com
- hxxp://statsrichwor{Removed}.com/def.exe
- hxxp://statsrichwor{Removed}.com/9sEdsV5D3P0eJclX/config.php
- hxxp://statsrichwor{Removed}.com/9sEdsV5D3P0eJclX/gate.php
- hxxp://www.hrk-ramo{Removed}.com
- hxxp://www.holzboc{Removed}.biz
- hxxp://www.fliptra{Removed}.biz
- hxxp://www.pizca{Removed}.com
- hxxp://www.belvedere-locarn{Removed}.com
- hxxp://www.seitenspringzimmer2{Removed}.com
- hxxp://www.arbezie-hote{Removed}.com
- hxxp://www.aubergemontblan{Removed}.com
- hxxp://www.aparthotelzuric{Removed}.com
- hxxp://www.bnbdelacollin{Removed}.com
- hxxp://www.waageglaru{Removed}.com
- hxxp://www.le-saint-huber{Removed}.com
- hxxp://www.hotelcher{Removed}.com
- hxxp://www.osteriadelcentr{Removed}.net
- hxxp://www.hoteldreirose{Removed}.net
- hxxp://www.gemperl{Removed}.net
- hxxp://www.calist{Removed}.net
- hxxp://www.r-coiffur{Removed}.net
- hxxp://www.nett-coiffur{Removed}.ch
- hxxp://www.farbech{Removed}.net
- hxxp://www.haaratelie{Removed}.net
- hxxp://www.von-ar{Removed}.net
- hxxp://www.kakaocor{Removed}.link
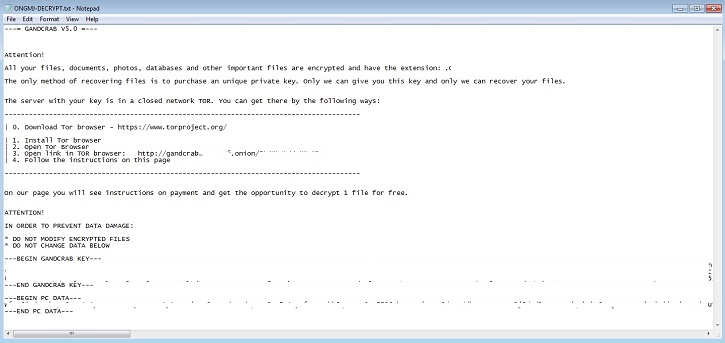
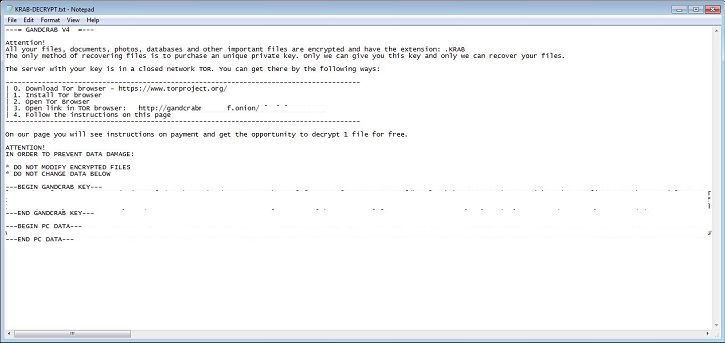
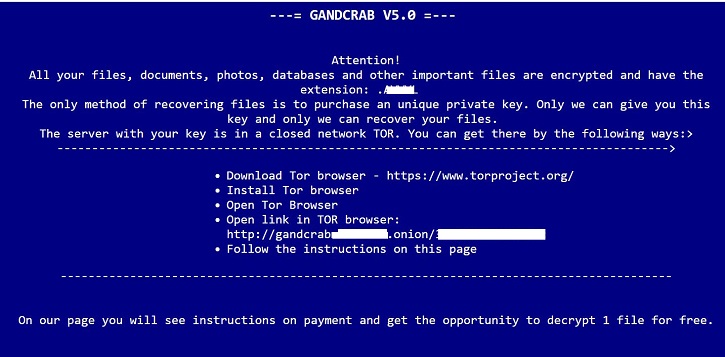
- Below are sample illustrations of the Ransomware notes:
 Analysis
Analysis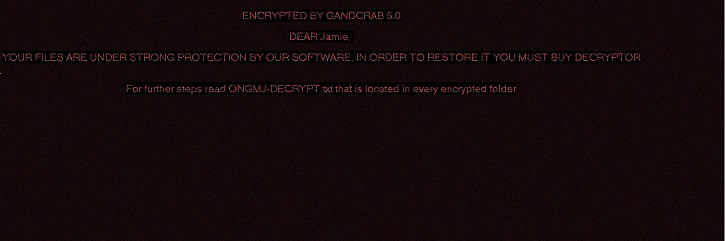
 Recommended Action
Recommended Action Telemetry
Telemetry