W32/WannaCry.7E25!tr.ransom
 Analysis
Analysis
W32/WannaCry.7E25!tr.ransom is a detection for a Ransomware WannaCry trojan.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- !please read me!.txt : This file is dropped in every infected folder. It will serve as ransom notes.
- COMO-RECUPERAR-TU-INFORMACION.txt : This file is dropped on the user's Desktop. It will serve as a ransom note.
- @please_read_me@.txt : This file is dropped in every infected folder. It will serve as ransom notes.
- !wannadecryptor!.exe.lnk : This file is dropped in every infected folder.It will serve as ransom notes.
- %CurrentPath%\!wannadecryptor!.exe : This fie is data file and will serve as ransom notes.
- %CurrentPath%\@wanadecryptor@.bmp: This data will serve as ransom notes.
- %CurrentPath%\TaskHost : This is a folder that contains several non-malicious tmp and TOR files.
- %CurrentPath%\c.wry : This file is non-malicious data file.
- %CurrentPath%\f.wry : This file is non-malicious data file.
- %CurrentPath%\m.wry : This file is non-malicious data file.
- %CurrentPath%\r.wry : This file is non-malicious data file.
- %CurrentPath%\t.wry : This file is non-malicious data file.
- %CurrentPath%\u.wry : This file is non-malicious data file.
- %CurrentPath%\c.vbs : This Visual Basic Script file creates shortcut to !wannadecryptor!.exe file.
- %CurrentPath%\m.vbs : This Visual Basic Script file creates shortcut to !wannadecryptor!.exe file.
- %CurrentPath%\x.vbs : This Visual Basic Script file attempts to run itself.
- %CurrentPath%\XXXXXXXXXXXXXXX.bat : This bat intends to drop the %CurrentPath%\c.vbs file.
- %CurrentPath%\00000000.pky : This file is non-malicious data file.
- %CurrentPath%\00000000.eky : This file is non-malicious data file.It contains encrypted private key.
- %CurrentPath%\00000000.res : This file contains information such as unique user ID, total encrypted file count, and total encrypted file size etcetera .
- %CurrentPath%\taskdl.exe : This file is detected as W32/Generic.AC.3F04F9!tr.
- %CurrentPath%\taskse.exe : This file is detected as W32/WannaCryptor.D!tr.ransom.
- @wanadecryptor@.exe: This file is dropped in every infected folder. This file is detected as W32/WannaCryptor.D!tr.ransom.
- %CurrentPath%\msg: This folder contains ransom notes in different languages.
- Affected victims of this Ransomware may be told to contact the following email address(es):
- hispahack@tutanota.com
- This Ransomware also changes desktop background to ransom notes using %CurrentPath%\@wanadecryptor@.bmp .
- This ransomware targets the following files:
- .123
- .3dm
- .3ds
- .3g2
- .3gp
- .602
- .7z
- .ARC
- .PAQ
- .accdb
- .aes
- .ai
- .asc
- .asf
- .asm
- .asp
- .avi
- .backup
- .bak
- .bat
- .bmp
- .brd
- .bz2
- .cgm
- .class
- .cmd
- .cpp
- .crt
- .cs
- .csr
- .csv
- .db
- .dbf
- .dch
- .der
- .dif
- .dip
- .djvu
- .doc
- .docb
- .docm
- .docx
- .dot
- .dotm
- .dotx
- .dwg
- .edb
- .eml
- .fla
- .flv
- .frm
- .gif
- .gpg
- .gz
- .hwp
- .ibd
- .iso
- .jar
- .java
- .jpeg
- .jpg
- .js
- .jsp
- .key
- .lay
- .lay6
- .ldf
- .m3u
- .m4u
- .max
- .mdb
- .mdf
- .mid
- .mkv
- .mml
- .mov
- .mp3
- .mp4
- .mpeg
- .mpg
- .msg
- .myd
- .myi
- .nef
- .odb
- .odg
- .odp
- .ods
- .odt
- .onetoc2
- .ost
- .otg
- .otp
- .ots
- .ott
- .p12
- .pas
- .pem
- .pfx
- .php
- .pl
- .png
- .pot
- .potm
- .potx
- .ppam
- .pps
- .ppsm
- .ppsx
- .ppt
- .pptm
- .pptx
- .ps1
- .psd
- .pst
- .rar
- .raw
- .rb
- .rtf
- .sch
- .sh
- .sldm
- .sldx
- .slk
- .sln
- .snt
- .sql
- .sqlite3
- .sqlitedb
- .stc
- .std
- .sti
- .stw
- .suo
- .svg
- .swf
- .sxc
- .sxd
- .sxi
- .sxm
- .sxw
- .tar
- .tbk
- .tgz
- .tif
- .tiff
- .txt
- .uop
- .uot
- .vb
- .vbs
- .vcd
- .vdi
- .vmdk
- .vmx
- .vob
- .vsd
- .vsdx
- .wav
- .wb2
- .wk1
- .wks
- .wma
- .wmv
- .xlc
- .xlm
- .xls
- .xlsb
- .xlsm
- .xlsx
- .xlt
- .xltm
- .xltx
- .xlw
- .zip
- This Ransomware also changes desktop background to ransom notes using %CurrentPath%\@wanadecryptor@.bmp .
- Affected files of this Ransomware will use the filenaming format:
- {Original name}.WCRY
- {Original name}.WNCRY
- This Ransomware attempts to delete the Shadow Volume copies so that user cannot restore them.
- This malware may apply any of the following registry modification(s):
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- Microsoft update task scheduler = %CurrentPath%\{OriginalMalwareFile} /r
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\Run
- Below is an illustration of the malware's Ransom notes:
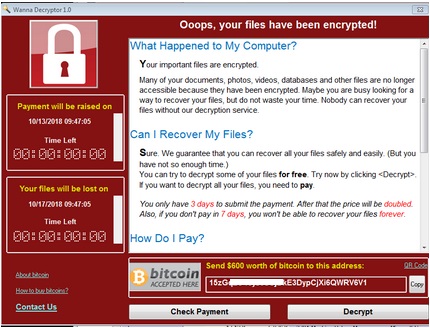
- Figure 1: Ransom notes.
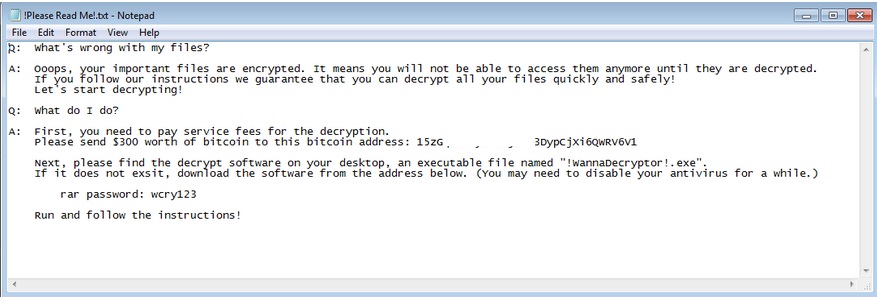
- Figure 2: Ransom notes.
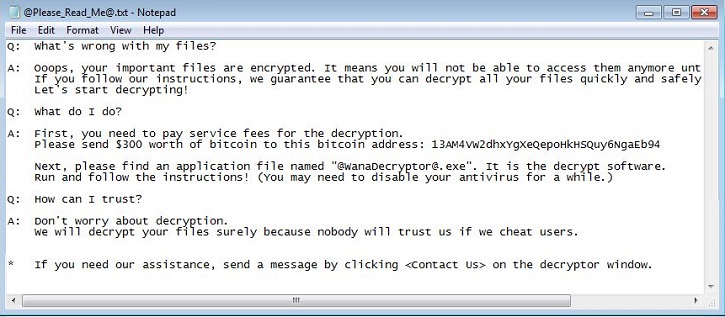
- Figure 3: Ransom notes.

- Figure 4: Ransom note from :%currentpath%\msg\m_english.wnry file.
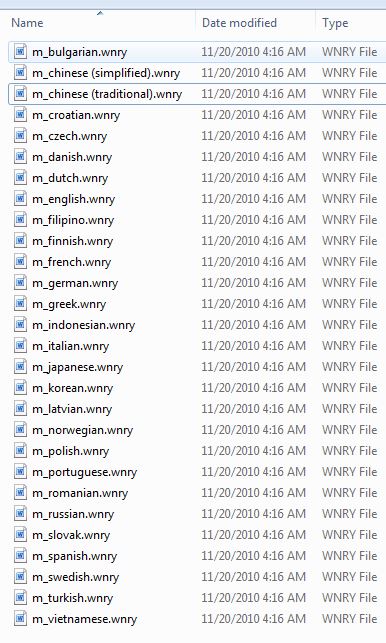
- Figure 5: Folder showing ransom notes in different languages: %currentpath%\msg\.
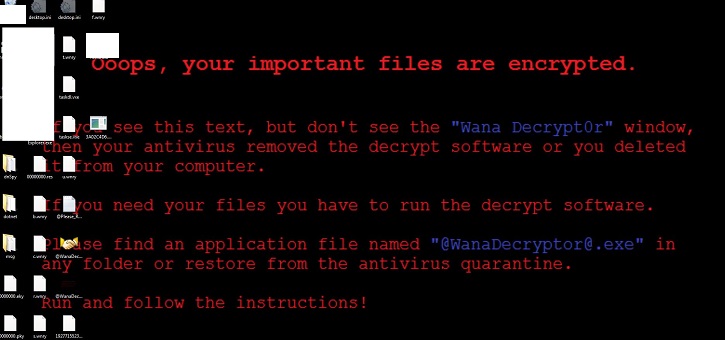
- Figure 6: Ransom note.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |