MSIL/Ghost.C3C4!tr.ransom
 Analysis
Analysis
MSIL/Ghost.C3C4!tr.ransom is a detection for Ghost Ransomware trojan.
Below are some of its observed characteristics/behaviours:
- %AppData%\ghost\ghost.bat : This batch file creates a service named ghostservice using the file ghostservice.exe
- %AppData%\ghost\ghostservice.exe : This file is .Dotnet file and detected as MSIL/Ghost.2566!tr.ransom .
- %AppData%\ghost\ghostservice.exe.config : This file is non-malicious data file.
- %AppData%\ghost\ghostservice.pdb : This file is currently analyzed as none malicious.
- %AppData%\ghost\ghostservice.vshost.exe : This is a legit .Net digital signed file and a product of Microsoft Visual Studio 2012.
- %AppData%\ghost\ghosthammer.dll : This file is currently detected as MSIL/Ghost.C3C4!tr, the file appears to be associated as encryption utility.
- %SystemDrive%\do_not_delete_codeid.txt : This file is a text file that contains the unique identifier to identify the infection.
- %SystemDrive%\ghostform.exe : This file is currently analyzed as none malicious.
- %SystemDrive%\ghosthammer.dll : This file is currently detected as MSIL/Ghost.C3C4!tr, the file appears to be associated as encryption utility.
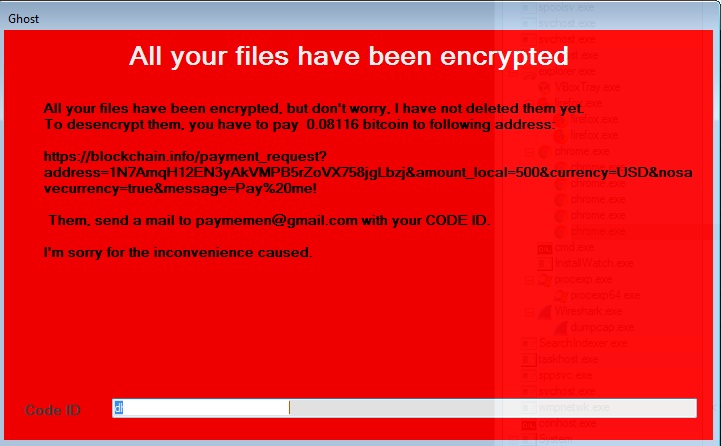
- paymemen@gmail.com
- hxxp://blockchain[.]info/payment_request?address
- www[.]12312312eewfef231[.]com
- .mdf
- .txt
- .bat
- .dot
- .doc
- .wbk
- .docx
- .pst
- .docm
- .dotm
- .xls
- .xlt
- .xlsx
- .xlm
- .xlsm
- .ppt
- .ldf
- .pps
- .pptx
- .accdb
- .accde
- .pub
- .xps
- .mp3
- .mp4
- .wav
- .wma
- .mpa
- .7z
- .rar
- .zip
- .iso
- .tar
- .gz
- .csv
- .mdb
- .sql
- .xml
- .db
- .dbf
- .jar
- .ai
- .bmp
- .mdf
- .gif
- .ico
- .jpg
- .png
- .jpeg
- .tif
- .tiff
- .svg
- .js
- .html
- .php
- .css
- •.cs
- .class
- .vb
- .bak
- .ink
- .avi
- HKEY_LOCAL_MACHINE\System\Controlset001\Services\Ghostservice
- Imagepath = %AppData%\ghost\ghostservice.exe
|
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |