W32/RaRansomware.2E5B!tr.ransom
 Analysis
Analysis
W32/RaRansomware.2E5B!tr.ransom is a generic detection for Ra Ransomware trojan.
Since this is a generic detection, this malware may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- %AppData%\xxxxx\xxxxx.exe : This file is a copy of the original malware itself. Here x is any lowercase alphabet.
- %AppData%\xxxxx\public.key : This file is non-malicious and contains public key for the infected system.
- %AppData%\xxxxx\private.enc : This file is non-malicious. This is a data file.
- %CurrentPath%\README IMPORTANT.html: This html file will serve as ransom notes.
- %CurrentPath%\README IMPORTANT.txt: This text file will serve as ransom notes.
- %CurrentPath%\PERSONAL-ID.txt: This text file contains the ID unique to the victim.
- Affected files of this Ransomware will use the file naming format [Random].xxxxx, where X is any lowercase alphabet.
- This malware was also observed to affect/encrypt files located on shared drive within the same subnet.
- This malware was also observed to affect/encrypt files located on USB or external drives.
- This malware attempts to inject PE image to the other processes.
- This malware may apply any of the following registry modification(s):
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- xxxxx = %AppData%\xxxxx\xxxxx.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- This malware may connect to any of the following remote sites(s):
- 8{Removed}.99.66.31
- 2n{Removed}.co
- Below is an illustration of the malware's Ransom notes:
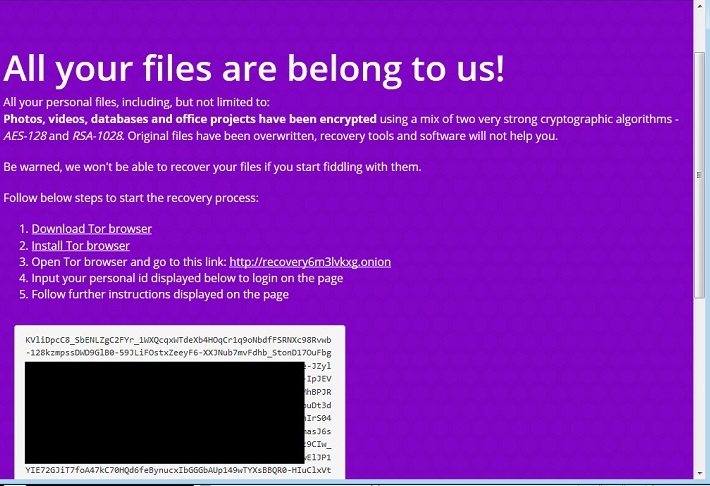
- Figure 1: Ransom Notes.
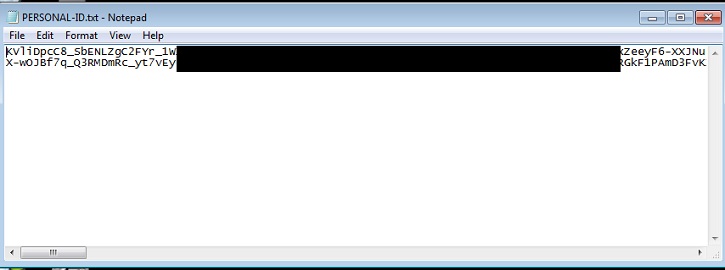
- Figure 2: Ransom notes .
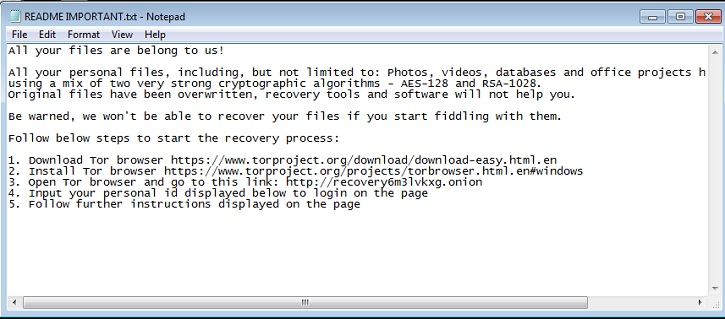
- Figure 3: Unique ID .
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiClient | |
|---|---|
| Extreme | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |