MSIL/ExoticSquad.FBA4!tr.ransom
 Analysis
Analysis
MSIL/ExoticSquad.FBA4!tr.ransom is a detection for a Exotic Squad Ransomware trojan.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- %StartUp%\svchost.exe : This file is a copy of the original malware itself.
- %Temp%\Image.png: This image file will serve as ransom note. This image is downloaded from hxxp://mitteode{Removed}.de/image.png.
- This Ransomware also changes desktop background to ransom notes using %Temp%\Image.png .
- Affected files of this Ransomware will use the filenaming format [Random].exotic
- This Ransomware encrypts the following file extensions:
- .txt .exe .text .cur .contact .ani .xls .com .url .ppt .src .cmd .tgz .fon .pl .lib .load .CompositeFont .png .exe .mp3
- .mkv .veg .mp4 .lnk .zip .rar .7z .jpg .sln .crdownload .msi .vb .vbs .vbt .config .settings .resx .vbproj .json .jpeg
- .scss .css .html .hta .ttc .ttf .eot .camproj .m4r .001 .002 .003 .004 .005 .006 .007 .008 .009 .au .aex .8be .8bf .8bi
- .abr .adf .apk .ai .asd .bin .bat .gif .3dm .3g2 .exe .3gp .aaf .accdb .aep .aepx .aet .ai .aif .arw .as .as3 .asf
- .asp .asx .avi .bay .bmp .cdr .cer .class .cpp .contact .cr2 .crt .crw .cs .csv .dll .db .dbf .dcr .der .dng .doc .docb
- .docm .docx .dot .dotm .dotx .dwg .dxf .dxg .efx .eps .erf .fla .flv .iso .idml .iff .ini .sik .indb .indd .indl .indt
- .ico .inx .jar .jnt .jnt .java .key .kdc .m3u .m3u8 .m4u .max .mdb .mdf .mef .mid .mov .mpa .mpeg .mpg .mrw .msg .nef
- .nrw .odb .odc .odm .odp .ods .odt .orf .p12 .p7b .p7c .pdb .pdf .pef .pem .pfx .php .plb .pmd .pot .potm .potx .ppam
- .ppj .pps .ppsm .ppsx .ppt .pptm .pptx .prel .prproj .ps .psd .pst .ptx .r3d .ra .raf .raw .rb .rtf .rw2 .rwl .sdf .sldm
- .sldx .sql .sr2 .srf .srw .svg .swf .tif .vcf .vob .wav .wb2 .wma .wmv .wpd .wps .x3f .xla .xlam .xlk .xll .xlm .xls .xlsb
- .xlsm .xlsx .xlt .xltm .xltx .xlw .xml .xqx
- This ransomware displays a message prompt upon execution and will await the user click of the "Ok" button before beginning its payload effects.
- This ransomware has an anti-sandbox function. It checks for the SandboxieRpcSs.exe process on the victim's sytem and shows Sandboxie error.
- This Ransomware kills the following processes:
- taskmgr
- cmd
- procexp
- procexp64
- regedit
- CCleaner64
- msconfig
- This Ransomware encrypts the files only from the following specified folders:
- %UserProfile%\MyPictures
- %UserProfile%\Desktop
- %UserProfile%\MyMusic
- %UserProfile%\Personal
- %UserProfile%\MyVideos
- %UserProfile%\Contacts
- %UserProfile%\Downloads
- /vmware-host/
- This malware may connect to any of the following remote sites(s):
- hxxp://mitteode{Removed}.de/image.png
- Below are some illustrations of this malware:
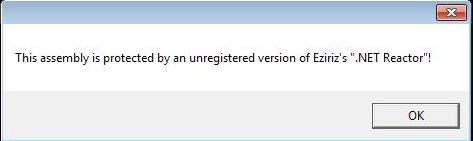
- Figure 1: Message prompt .
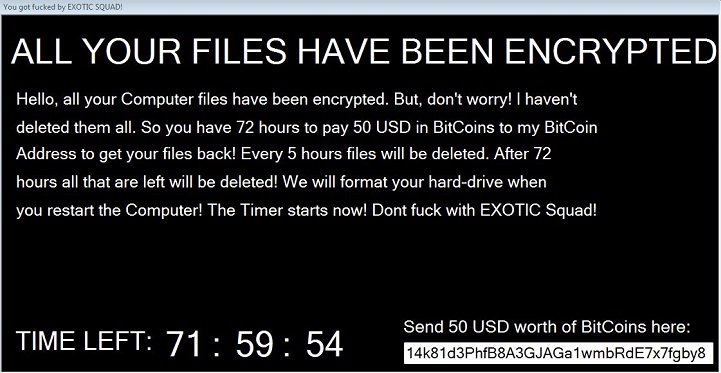
- Figure 2: Ransom note .
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |