W32/Cypher.F308!tr.ransom
 Analysis
Analysis
W32/Cypher.F308!tr.ransom is a detection for a Ransomware Cipher trojan.
Below are some of its observed characteristics/behaviours:
- This malware may drop any of the following file(s):
- HOW_TO_DECRYPT_FILES.html : This html file is dropped in every infected folder and will serve as ransom note.
- %AppData%\[Random2].exe : This file is the copy of the original malware itself.
- %AppData%\encryption_key : This file contains a set of encryption keys for the infected system.
- Affected files of this Ransomware may use one of the following filenaming formats:
- {OriginalFilename.Ext}.cypher
- {OriginalFilename.Ext}.xcry7684
- This malware was also observed to affect/encrypt files located on shared drive within the same subnet.
- This malware was also observed to affect/encrypt files located on USB or external drives.
- Affected victims of this Ransomware are redirected by the attacker via:
- biggsurprise@tutanota.com
- ochennado@tutanota.com
- funnybtc@airmail.cc
- This malware may apply any of the following registry modification(s):
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- [Random1] = %AppData%\[Random2].exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\Currentversion\Run
- Below is an illustration of the malware's Ransom notes:
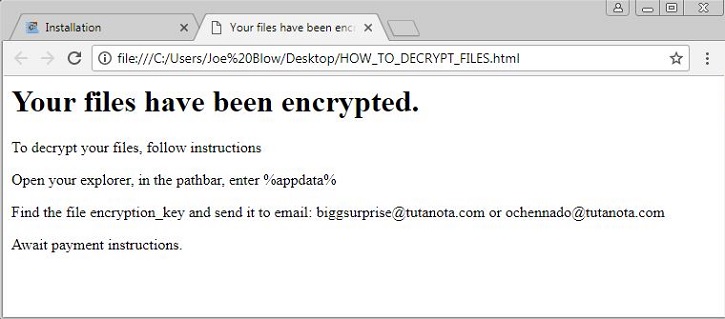
- Figure 1: Ransom note.
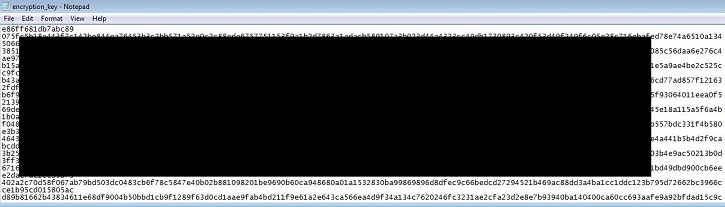
- Figure 2: Encryption key file.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |