New Agent Tesla variant in the wild
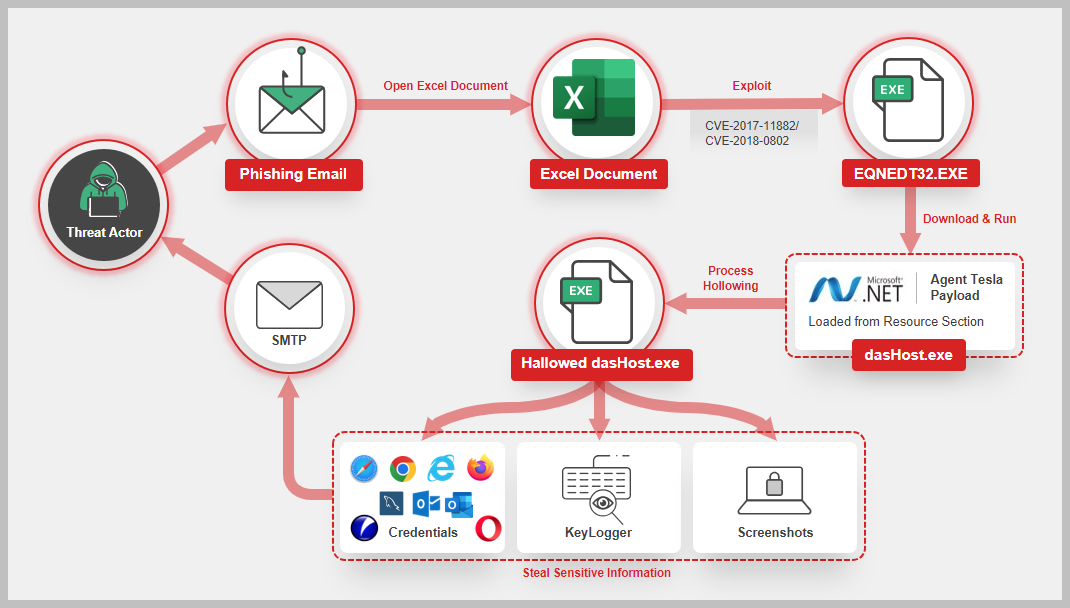
FortiGuard Labs captured a phishing campaign that spreads a new Agent Tesla variant. This well-known malware family uses a .Net-based Remote Access Trojan (RAT) and data stealer to gain initial access by exploiting vulnerabilities Microsoft Office vulnerabilities CVE-2017-11882 and CVE-2018-0802. The Agent Tesla core module can collect sensitive information from the victim’s device that may include the saved credentials, keylogging information, and device screenshots.. Learn More »
Common Vulnerabilities and Exposures
Background
Agent Tesla made its debut in 2014, and since then, numerous iterations of this malware have been released. This malware employs various tactics to avoid detection, rendering the process of analysis challenging. Agent Tesla is typically spread through phishing emails and has a range of capabilities, including keylogging, screen capture, form-grabbing, and the theft of credentials, among others. Additionally, it has the ability to gather credentials from various software programs, such as Google Chrome, Mozilla Firefox, and Microsoft Outlook, thereby significantly amplifying its potential for causing severe damage.
CVE-2017-11882 and CVE-2018-0802 are RCE (Remote Code Execution) vulnerabilities in Microsoft Office that can result in memory corruption inside the EQNEDT32.EXE process. In this particular case, CVE-2017-11882 and CVE-2018-0802 vulnerability is exploited to download and execute the Agent Tesla file on the victim’s device.
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
July, 2023: During late July this year, FortiGuard labs observed Agent Tesla's new variant being propagated and blocked automatically by Sandbox Behaviour engine. The telemetry shows a total of over 150 thousand blocked counts in July and August 2023.
September 05, 2023: FortiGuard Labs captured a phishing campaign that spreads a new Agent Tesla variant and released a detailed analysis blog on;
https://www.fortinet.com/blog/threat-research/agent-tesla-variant-spread-by-crafted-excel-document
Vulnerabilities (CVE-2017-11882 and CVE-2018-0802) remains popular amongst threat actors, suggesting there are still unpatched devices in the wild, even after over five years. FortiGuard Labs observed and blocked over 3000+ attacks per day, at the IPS level and the number of observed vulnerable devices according to FortiGuard telemetry is around 1300+.
Fortinet customers remain protected from this campaign and other variants of Agent Tesla by FortiGuard’s AntiSPAM, IPS, Web Filtering, AntiVirus services, and Behaviour Engine (AI/ML) services. As mentioned on the released Blog earlier, FortiGuard continue to recommend users and organizations to go through the NSE training: NSE 1 – Information Security Awareness, a module on Internet threats designed to help end users learn how to identify and protect themselves from phishing attacks and other best practices.
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
AV
-
Anti-spam
-
Vulnerability
-
AV (Pre-filter)
-
Behavior Detection
-
IPS
-
Web & DNS Filter
-
Botnet C&C
-
Outbreak Detection
-
Threat Hunting
-
IOC
-
Content Update
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Vulnerability Management
-
Attack Surface Hardening
-
Business Reputation
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
References
Sources of information in support and relation to this Outbreak and vendor.